DGS-1250 Series Gigabit Ethernet Smart Managed Switch Web UI Reference Guide
37
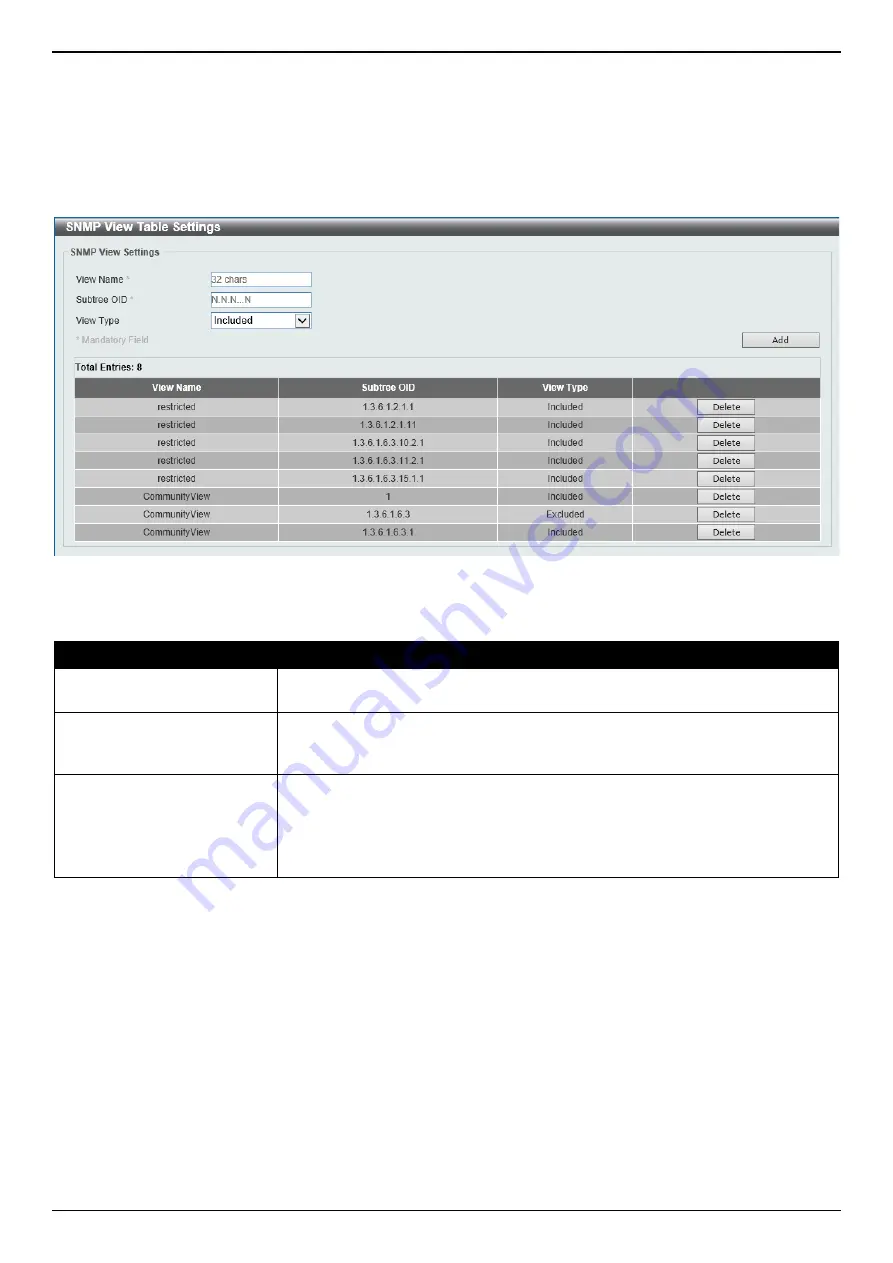
SNMP View Table Settings
This window is used to assign views to community strings that define which MIB objects can be accessed by a remote
SNMP manager. The SNMP sub-tree OID created with this table maps SNMP users to the views created in the
SNMP
User Table Settings
window.
To view the following window, click
Management > SNMP > SNMP View Table Settings
, as shown below:
Figure 4-5 SNMP View Table Settings Window
The fields that can be configured are described below:
Parameter
Description
View Name
Type an alphanumeric string of up to 32 characters. This is used to identify the
new SNMP view being created.
Subtree OID
Type the Object Identifier (OID) sub-tree for the view. The OID identifies an object
tree (MIB tree) that will be included or excluded from access by an SNMP
manager.
View Type
Select the view type here. Options to choose from are
Included
and
Excluded
.
•
Included
- Select to include this object in the list of objects that an SNMP
manager can access.
•
Excluded
- Select to exclude this object from the list of objects that an
SNMP manager can access.
Click the
Add
button to add a new entry based on the information entered.
Click the
Delete
button to remove the specified entry.
SNMP Community Table Settings
This window is used to create an SNMP community string to define the relationship between the SNMP manager and
an agent. The community string acts like a password to permit access to the agent on the Switch. One or more of the
following characteristics can be associated with the community string:
•
An access list containing IP addresses of SNMP managers that are permitted to use the community string to
gain access to the Switch’s SNMP agent.
•
Any MIB view that defines the subset of MIB objects that will be accessible to the SNMP community.
•
Read-write or read-only level permissions for the MIB objects accessible to the SNMP community.
Summary of Contents for DGS-1250 Series
Page 1: ......






























