DGS-1250 Series Gigabit Ethernet Smart Managed Switch Web UI Reference Guide
208
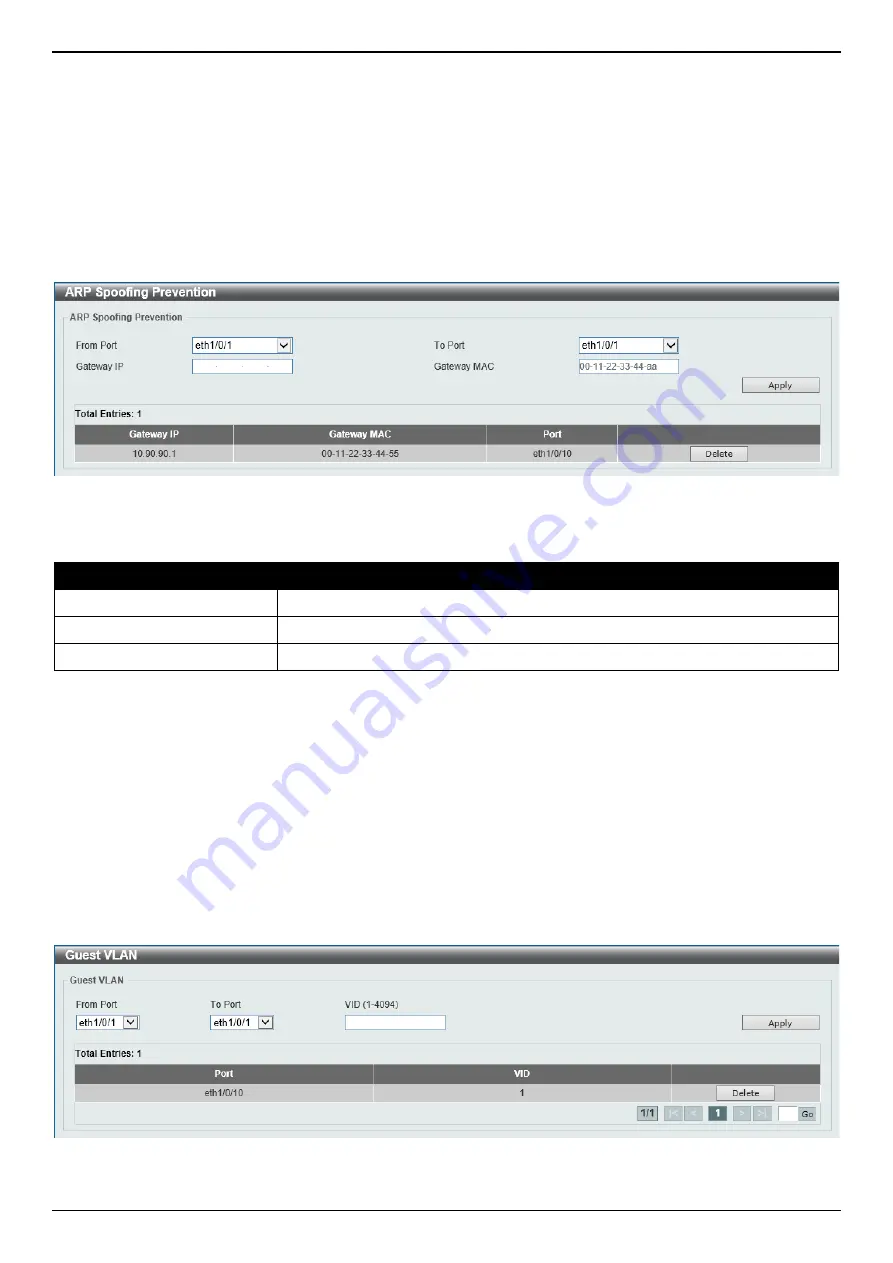
ARP Spoofing Prevention
This window is used to display and configure the ARP spoofing prevention settings. When an entry is created, ARP
packets whose sender IP address matches the gateway IP address, of an entry, but its sender MAC address field
does not match the gateway MAC address, of the entry, will be dropped by the system. The ASP will bypass the ARP
packets whose sender IP address doesn’t match the configured gateway IP address.
If an ARP address matches a configured gateway’s IP address, MAC address, and port list, then bypass the Dynamic
ARP Inspection (DAI) check no matter if the receiving port is ARP trusted or untrusted.
To view the following window, click
Security > ARP Spoofing Prevention
, as shown below:
Figure 9-52 ARP Spoofing Prevention Window
The fields that can be configured in
ARP Spoofing Prevention
are described below:
Parameter
Description
From Port - To Port
Select the appropriate port range used for the configuration here.
Gateway IP
Enter the gateway IP address used here.
Gateway MAC
Enter the gateway MAC address used here.
Click the
Apply
button to accept the changes made.
Click the
Delete
button to remove the specified entry.
Network Access Authentication
Guest VLAN
This window is used to display and configure the network access authentication guest VLAN settings.
To view the following window, click
Security > Network Access Authentication > Guest VLAN
, as shown below:
Figure 9-53 Guest VLAN Window
Summary of Contents for DGS-1250 Series
Page 1: ......






























