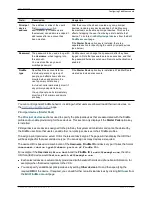
Groups belonged to
Access permissions granted
Administrators
and
Region B
read-write access to the API interface, but no web interface access
Administrators
and
Region C
read-write access to the web and API interfaces
Region A
only
read-only access to the web interface and no API access
Configuring FindMe groups
The
FindMe groups
page (
Users > FindMe groups
) lists all the FindMe groups that have been configured
on the VCS, and lets you add, edit and delete groups.
Note that this page does not apply if the VCS is using
TMS Provisioning Extension services
to provide
FindMe account data; in this case, FindMe accounts are maintained through Cisco TMS.
n
FindMe groups are only active when
remote FindMe authentication
is enabled.
n
FindMe groups determine which access rights members of the group have after they have been
successfully authenticated to use the VCS.
When a FindMe user logs in to the VCS their credentials are authenticated against the remote directory
service and they are assigned the access rights associated with the group to which that user belongs. If the
user account belongs to more than one group, the highest level permission is assigned.
The configurable options are:
Field
Description
Usage tips
Name
The name of the FindMe group.
It cannot contain any of the following
characters:
/ \ [ ] : ; | = , + * ? > < @ "
The group names defined in the VCS must match the group
names that have been set up in the remote directory service to
manage FindMe accounts.
State
Indicates if the group is enabled or
disabled.
Enabled
: users can view and modify
their personal FindMe details,
devices and locations.
Disabled
: users are not allowed to log
in to their account.
Default:
Enabled
Cisco VCS Administrator Guide (X8.1.1)
Page 270 of 507
User accounts
Configuring remote account authentication using LDAP