22
Wireless-N Router
Linksys E1000
Chapter 2: Advanced Configuration
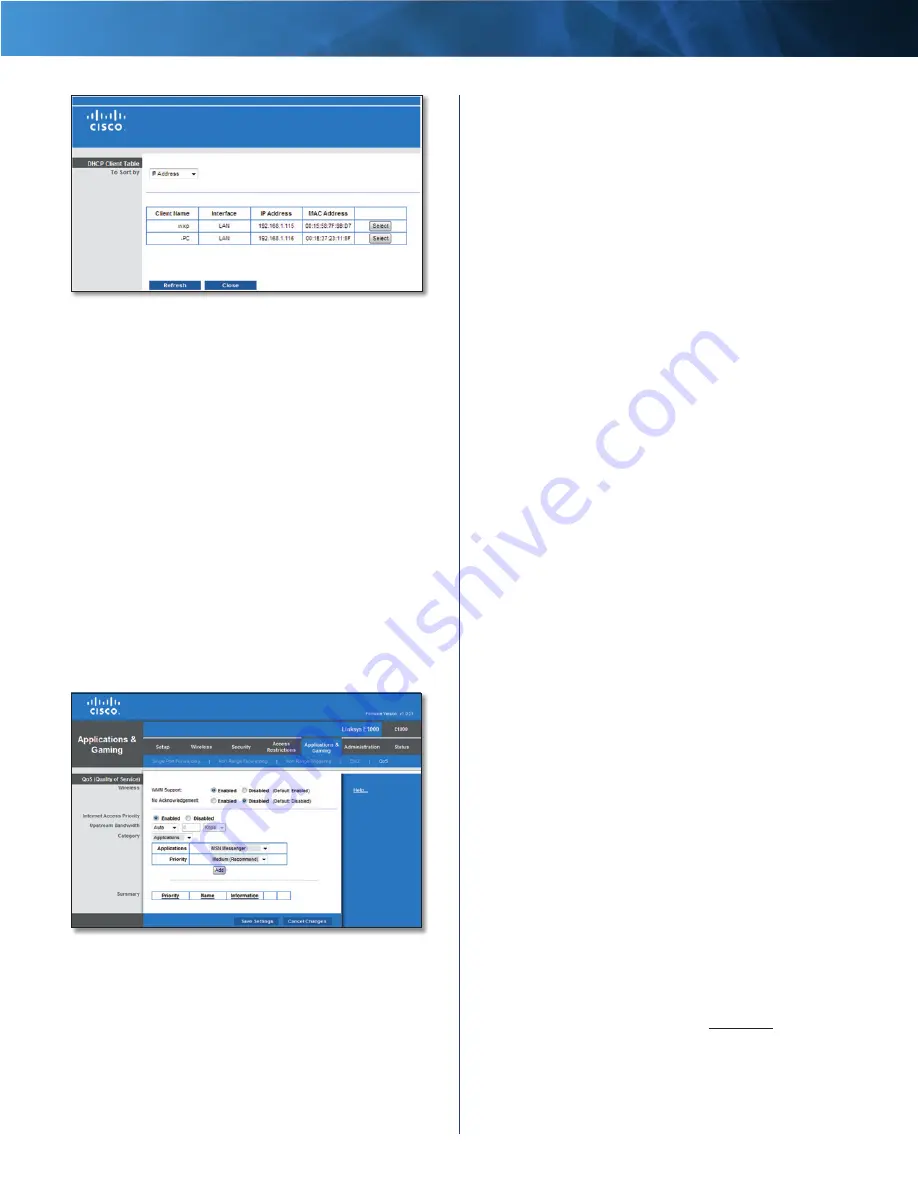
DMZ > DHCP Client Table
DHCP Client Table
The DHCP Client Table lists computers and other
devices that have been assigned IP addresses by the
Router . The list can be sorted by Client Name, Interface,
IP Address, and MAC Address . To select a DHCP client,
click Select . To update the on-screen information,
click Refresh . To exit this screen and return to the
DMZ
screen, click Close .
Click Save Settings to apply your changes, or click Cancel
Changes to clear your changes .
Applications and Gaming > QoS
Quality of Service (QoS) is a method that assigns priority
to specific types of network traffic, which often are
demanding, real-time applications, such as gaming,
videoconferencing, video streaming, and Voice over
Internet Protocol (VoIP) telephony . QoS helps to ensure
optimal performance for these types of uses .
Applications and Gaming > QoS
QoS (Quality of Service)
Wireless
WMM Support
Wi-Fi Multimedia (WMM) is a wireless
Quality of Service feature that improves quality for audio,
video, and voice applications by prioritizing wireless
traffic . To use this feature, the wireless client devices in
your network must support Wireless WMM . To disable
this option, select Disabled . Otherwise, keep the default,
Enabled .
No Acknowledgement
If you want to disable the
Router’s Acknowledgement option, so the Router will
not re-send data if an error occurs, then select Enabled .
Otherwise, keep the default, Disabled .
Internet Access Priority
In this section, you can set the bandwidth priority for a
variety of applications and devices . There are four levels
of priority: High, Medium, Normal, or Low . When you
set priority, do not set all applications to High, because
this will defeat the purpose of allocating the available
bandwidth . If you want to select below normal bandwidth,
select Low . Depending on the application, a few attempts
may be needed to set the appropriate bandwidth priority .
Enabled/Disabled
To use the QoS policies you set, select
Enabled . Otherwise, keep the default, Disabled .
Upstream Bandwidth
Upstream Bandwidth
This option sets the maximum
outgoing bandwidth that applications can use . To allow
the Router to set the maximum, keep the default, Auto .
To specify the maximum, select Manual . Then enter the
appropriate value and select Kbps or Mbps .
Category
You can define the Internet access priority level for as
many categories as you want . The
Summary
section will
display all of the priority selections that you enter . Select
from the following categories:
•
Applications
Allows you to assign a priority level for a
pre-defined application or one that you add .
•
Online Games
Allows you to assign a priority level for
a pre-defined game or one that you add .
•
MAC Address
This option lets you prioritize network
traffic based on the device that is accessing the
network . For example, if you want your gaming
console to have higher priority accessing the Internet
than your computer, you can assign their priority levels
using their respective MAC addresses .
•
Voice Device
Voice devices require a higher priority
level . You can assign a higher priority level to voice
devices using their respective MAC addresses .
Summary
This lists the QoS entries you have created for your
applications and devices . Refer to “Summary” on page 24
for more information .

























