11-11
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 11 Service Policy Using the Modular Policy Framework
Configure Service Policies
When used in a policy, this class ensures that the correct inspection is applied to each packet, based on
the destination port of the traffic. For example, when UDP traffic for port 69 reaches the ASA, then the
ASA applies the TFTP inspection; when TCP traffic for port 21 arrives, then the ASA applies the FTP
inspection. So in this case only, you can configure multiple inspections for the same class map.
Normally, the ASA does not use the port number to determine which inspection to apply, thus giving you
the flexibility to apply inspections to non-standard ports, for example.
class-map inspection_default
match default-inspection-traffic
Another class map that exists in the default configuration is called class-default, and it matches all
traffic. This class map appears at the end of all Layer 3/4 policy maps and essentially tells the ASA to
not perform any actions on all other traffic. You can use the class-default class if desired, rather than
making your own
match any
class map. In fact, some features are only available for class-default.
class-map class-default
match any
Configure Service Policies
To configure service policies using the Modular Policy Framework, perform the following steps:
Step 1
Identify the traffic
on which you want to act by creating Layer 3/4 class maps, as described in
Traffic (Layer 3/4 Class Maps), page 11-13
.
For example, you might want to perform actions on all traffic that passes through the ASA; or you might
only want to perform certain actions on traffic from 10.1.1.0/24 to any destination address.
Step 2
Optionally, perform additional actions on some inspection traffic.
If one of the actions you want to perform is application inspection, and you want to perform additional
actions on some inspection traffic, then create an inspection policy map. The inspection policy map
identifies the traffic and specifies what to do with it.
For example, you might want to drop all HTTP requests with a body length greater than 1000 bytes.
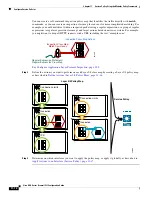
Layer
3
/4 Class Map
Layer
3
/4 Class Map
241506
Inspection Class Map/
Match Commands
Inspection Policy Map Actions
241507
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......