10-15
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 10 NAT Examples and Reference
NAT for VPN
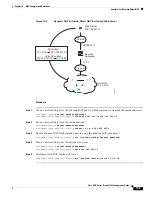
Figure 10-12
Routed Mode Egress Interface Selection
NAT for VPN
The following topics explain NAT usage with the various types of VPN.
•
NAT and Remote Access VPN, page 10-15
•
NAT and Site-to-Site VPN, page 10-17
•
NAT and VPN Management Access, page 10-19
•
Troubleshooting NAT and VPN, page 10-21
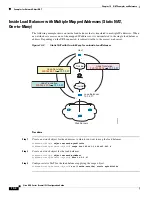
NAT and Remote Access VPN
The following figure shows both an inside server (10.1.1.6) and a VPN client (209.165.201.10) accessing
the Internet. Unless you configure split tunneling for the VPN client (where only specified traffic goes
through the VPN tunnel), then Internet-bound VPN traffic must also go through the ASA. When the VPN
traffic enters the ASA, the ASA decrypts the packet; the resulting packet includes the VPN client local
address (10.3.3.10) as the source. For both inside and VPN client local networks, you need a public IP
address provided by NAT to access the Internet. The below example uses interface PAT rules. To allow
the VPN traffic to exit the same interface it entered, you also need to enable intra-interface
communication (also known as “hairpin” networking).
Real: 10.1.1.78
Mapped: 209.165.201.08
Inside
Untranslation
Packet
Eng
Dest. 209.165.201.08
10.1.1.78
209.165.201.08
to
NAT rule specifies interface?
NAT rule specifies route lookup?
No
Yes
Yes
No
Send packet out Inside interface.
Where to send 10.1.1.78?
Outside
Look up 10.1.1.78 in routing table.
3
70049
Summary of Contents for ASA 5508-X
Page 11: ...P A R T 1 Access Control ...
Page 12: ......
Page 157: ...P A R T 2 Network Address Translation ...
Page 158: ......
Page 233: ...P A R T 3 Service Policies and Application Inspection ...
Page 234: ......
Page 379: ...P A R T 4 Connection Management and Threat Detection ...
Page 380: ......