26
2.8.5. System Security
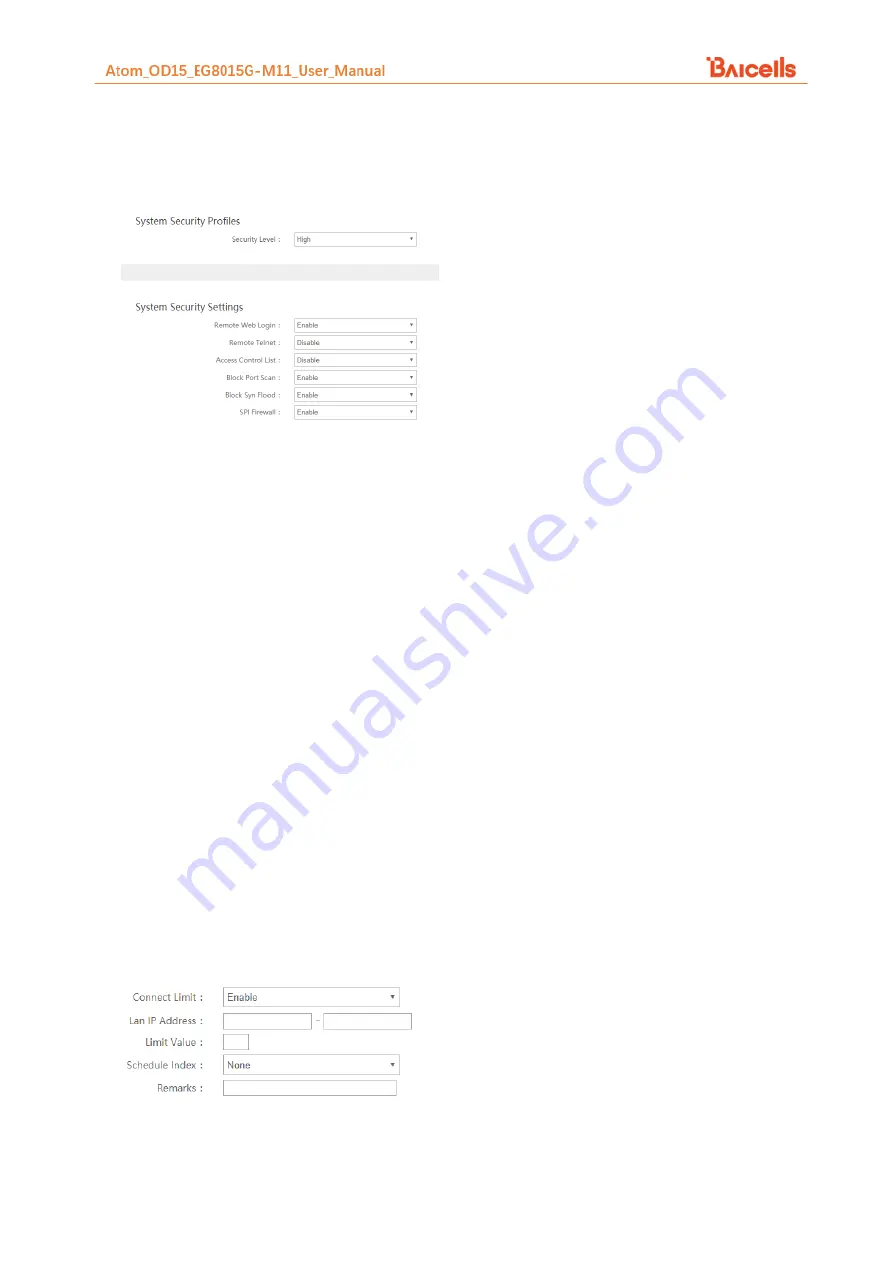
Figure 35: System Security
System Security Profiles, include High, Medium, None and Custom, every profiles will corresponding with a
set of System Security Settings.
Settings:
(1)
Remote Web Login: enable / disable
(2)
Remote Telnet: enable / disable
(3)
Access Control List: enable / disable
(4)
Block Port Scan: enable / disable
(5)
Block Syn Flood: enable / disable
(6)
SPI Firewall: enable / disable
2.8.6. Connect Limit
Connect Limit feature is used to control the number of connections through the UE to a host device, for
example, a peer-to-peer file sharing application such as BitTorrent. Such apps require a large amount of
bandwidth. By limiting the number of connections to the host device, you can control how much
bandwidth each active connection receives. You can configure a Connect Limit for up to 16 host devices.
Figure 36: Connect Limit












































