POEGEM24T4SFP
User
Manual
145
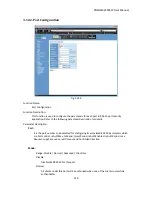
The
overview
of
operation
flow
for
the
Fig.
3
‐
144
is
quite
simple.
When
the
Supplicant
PAE
issues
a
request
to
the
Authenticator
PAE,
the
Authenticator
and
Supplicant
exchange
authentication
messages.
Then,
Authenticator
passes
the
request
to
RADIUS
server
to
verify.
Finally,
RADIUS
server
replies
if
the
request
is
granted
or
denied.
While
in
the
authentication
process,
the
message
packets,
encapsulated
by
Extensible
Authentication
Protocol
over
LAN
(EAPOL),
are
exchanged
between
an
authenticator
PAE
and
a
supplicant
PAE.
The
Authenticator
exchanges
the
messages
to
the
authentication
server
using
EAP
encapsulation.
Before
successfully
authenticating,
the
supplicant
can
only
access
the
authenticator
to
perform
authentication
message
exchange
or
access
the
network
from
the
uncontrolled
port.
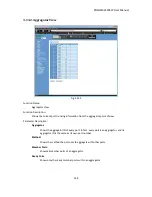
Fig.
3
‐
145
In
the
Fig.
3
‐
145,
this
is
the
typical
configuration,
a
single
supplicant,
an
authenticator
and
an
authentication
server.
B
and
C
is
in
the
internal
network,
D
is
Authentication
server
running
RADIUS,
switch
at
the
central
location,
it
acts
as
the
Authenticator
connecting
to
PC
A
and
A
is
a
PC
outside
the
controlled
port,
running
Supplicant
PAE.
In
this
case,
PC
A
wants
to
access
the
services
on
device
B
and
C,
first,
it
must
exchange
the
authentication
message
with
the
authenticator
on
the
port
it
is
connected
via
EAPOL
packet.
The
authenticator
transfers
the
supplicant’s
credentials
to
the
Authentication
server
for
verification.
If
successful,
the
authentication
server
will
give
the
authenticator
permission.
PC
A,
then,
is
allowed
to
access
B
and
C
via
the
switch.
If
there
are
two
switches
directly
connected
together
instead
of
a
single
one,
for
the
link
connecting
the
two
switches,
it
may
have
to
act
as
two
port
roles
at
the
end
of
the
link:
authenticator
and
supplicant,
because
the
traffic
is
bi
‐
directional.
LAN
Authenticator
PAE
Services Offered
by Authenticator
Authenticator’s System
Authentication
Server’s System
Authentication
Server
Supplicant
PAE
Supplicant’
s
Uncontrolled port
Controlled port
MAC Enable
Port
Authorize
Summary of Contents for POEGEM24T4SFP
Page 68: ...POEGEM24T4SFP User Manual 68 Move to the previous page Next Page Move to the next page...
Page 82: ...POEGEM24T4SFP User Manual 82 Fig 3 42 Fig 3 43 Fig 3 44...
Page 89: ...POEGEM24T4SFP User Manual 89 Fig 3 48...
Page 106: ...POEGEM24T4SFP User Manual 106 Fig 3 71 Fig 3 72...
Page 108: ...POEGEM24T4SFP User Manual 108 Fig 3 75 Fig 3 76 Fig 3 77 ARP...
Page 109: ...POEGEM24T4SFP User Manual 109 Fig 3 78 ARP Fig 3 79 ARP Fig 3 80 ARP Fig 3 81 ARP...
Page 110: ...POEGEM24T4SFP User Manual 110 Fig 3 82 ARP Fig 3 83 ARP Fig 3 84 ARP Fig 3 85 ARP...
Page 111: ...POEGEM24T4SFP User Manual 111 Fig 3 86 ARP Fig 3 87 ARP Fig 3 88 ARP Fig 3 89 ARP Fig 3 90 ARP...
Page 112: ...POEGEM24T4SFP User Manual 112 Fig 3 91 IPv4 Fig 3 92 IPv4 Fig 3 93 IPv4...
Page 115: ...POEGEM24T4SFP User Manual 115 Fig 3 105 IPv4 Fig 3 106 IPv4 Fig 3 107 IPv4...
Page 116: ...POEGEM24T4SFP User Manual 116 Fig 3 108 IPv4 Fig 3 109 IPv4 Fig 3 110 IPv4...
Page 117: ...POEGEM24T4SFP User Manual 117 Fig 3 111 IPv4 Fig 3 112 IPv4 Fig 3 113 IPv4 Fig 3 114 IPv4...
Page 118: ...POEGEM24T4SFP User Manual 118 Fig 3 115 IPv4 Fig 3 116 IPv4 Fig 3 117 IPv4...
Page 119: ...POEGEM24T4SFP User Manual 119 Fig 3 118 IPv4 Fig 3 119 IPv4 Fig 3 120 IPv4...
Page 120: ...POEGEM24T4SFP User Manual 120 Fig 3 121 Action Fig 3 122 Rate Limiter...
Page 121: ...POEGEM24T4SFP User Manual 121 Fig 3 123 Port Copy Fig 3 124 DMAC Filter...
Page 211: ...POEGEM24T4SFP User Manual 211 Fig 4 3...
Page 238: ...POEGEM24T4SFP User Manual 238 2 1 3 1 4 1 5 1 POEGEM24T4SFP acl...