1-2
PoE Features Supported by the Device
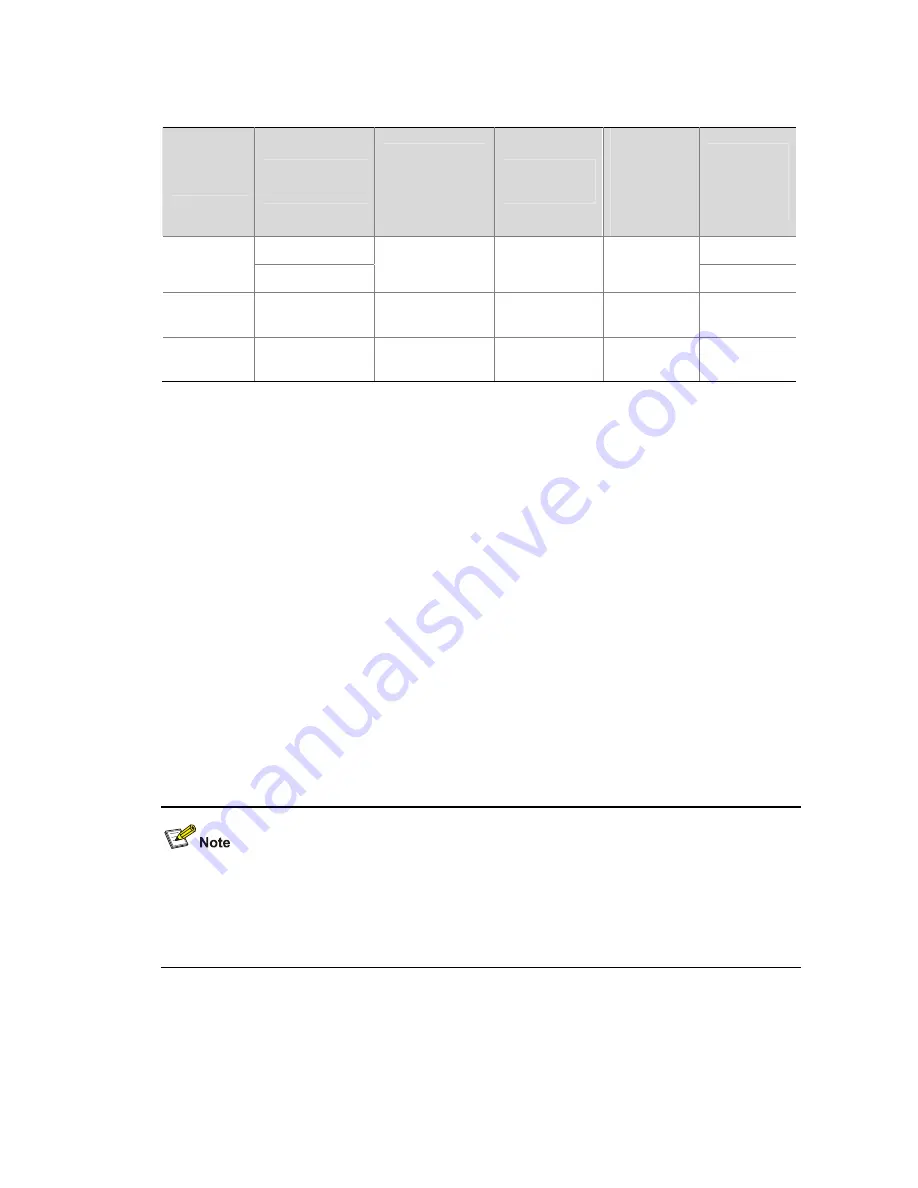
Table 1-1
Power supply parameters of PoE device
Device
Input power
supply
Number of
electrical ports
supplying
power
Maximum
PoE distance
Maximum
power
provided by
each
electrical
port
Total
Maximum
PoE output
power
DC input
600 W
WX3024
AC input
24
100 m (328.08
ft.)
25 W
370 W
WX3010 DC
input
8
100 m (328.08
ft.)
25 W
125 W
WX3008 DC
input
4
100 m (328.08
ft.)
25 W
125 W
A PoE-enabled device has the following features:
z
As the PSE, it supports the IEEE802.3af standard. It can also supply power to some PDs that do
not support the 802.3af standard.
z
It can deliver data and current simultaneously through data wires (1,2,3,6) of category-3/5 twisted
pairs.
z
The PSE processing software on the device can be upgraded online.
z
The device provides statistics about power supplying on each port and the whole equipment, which
you can query through the
display
command.
z
The device provides two modes (
auto
and
manual
) to manage the power feeding to ports in the
case of PSE power overload.
z
The device provides over-temperature protection mechanism. When the internal temperature of
the device exceeds the PoE protection temperature, the device disables the PoE feature on all
ports for self-protection.
z
The device supports the PoE profile feature, that is, different PoE policies can be set for different
user groups. These PoE policies are each saved in the corresponding PoE profile and applied to
ports of the user groups.
z
When you use the PoE-enabled device to supply power, the PDs need no external power supply.
z
If a remote PD has an external power supply, the PoE-enabled device and the external power
supply will backup each other for the PD.
z
Only the Ethernet electrical ports of the PoE-enabled device support the PoE feature.
PoE Configuration
PoE Configuration Task List
Complete the following tasks to configure PoE:






























