ZyWALL 5 User’s Guide
Chapter 14 VPN Screens
245
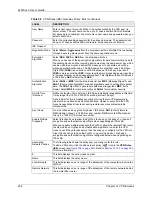
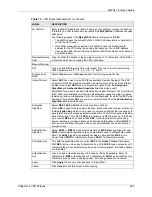
My ZyWALL
Enter the WAN IP address or domain name of your ZyWALL or leave the field set
to
0.0.0.0
. The VPN tunnel has to be rebuilt if the
My ZyWALL
IP address changes
after setup.
The following applies if the
My ZyWALL
field is configured as
0.0.0.0
:
•
The ZyWALL uses the current ZyWALL WAN IP address (static or dynamic) to
set up the VPN tunnel.
•
If the WAN connection goes down, the ZyWALL uses the dial backup IP
address for the VPN tunnel when using dial backup or the LAN IP address
when using traffic redirect. See the chapter on WAN for details on dial backup
and traffic redirect.
Remote Gateway
Addr
Type the WAN IP address or the domain name (up to 31 characters) of the IPSec
router with which you're making the VPN connection.
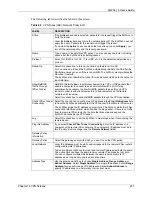
Manual Proposal
SPI
Type a unique
SPI
(Security Parameter Index) from one to four characters long.
Valid Characters are "0, 1, 2, 3, 4, 5, 6, 7, 8, and 9".
Encapsulation
Mode
Select
Tunnel
mode or
Transport
mode from the drop-down list box.
Active Protocol
Select
ESP
if you want to use ESP (Encapsulation Security Payload). The ESP
protocol (RFC 2406) provides encryption as well as some of the services offered
by
AH
. If you select
ESP
here, you must select options from the
Encryption
Algorithm
and
Authentication Algorithm
fields (described next).
Select
AH
if you want to use AH (Authentication Header Protocol). The AH protocol
(RFC 2402) was designed for integrity, authentication, sequence integrity (replay
resistance), and non-repudiation but not for confidentiality, for which the ESP was
designed. If you select
AH
here, you must select options from the
Authentication
Algorithm
field (described next).
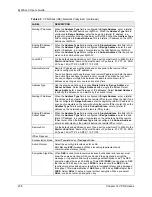
Encryption
Algorithm
Select
DES
,
3DES
or
NULL
from the drop-down list box.
When
DES
is used for data communications, both sender and receiver must know
the
Encryption Key
, which can be used to encrypt and decrypt the message or to
generate and verify a message authentication code. The DES encryption algorithm
uses a 56-bit key. Triple DES (
3DES
) is a variation on DES that uses a 168-bit key.
As a result,
3DES
is more secure than
DES
. It also requires more processing
power, resulting in increased latency and decreased throughput. Select
NULL
to
set up a tunnel without encryption. When you select
NULL
, you do not enter an
encryption key.
Authentication
Algorithm
Select
SHA1
or
MD5
from the drop-down list box.
MD5
(Message Digest 5) and
SHA1
(Secure Hash Algorithm) are hash algorithms used to authenticate packet
data. The
SHA1
algorithm is generally considered stronger than
MD5
, but is
slower. Select
MD5
for minimal security and
SHA-1
for maximum security.
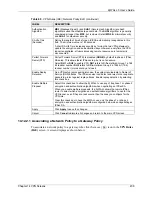
Encryption Key
This field is applicable when you select
ESP
in the
Active
Protocol
field above.
With
DES
, type a unique key 8 characters long. With
3DES
, type a unique key 24
characters long. Any characters may be used, including spaces, but trailing spaces
are truncated.
Authentication
Key
Type a unique authentication key to be used by IPSec if applicable. Enter 16
characters for
MD5
authentication or 20 characters for
SHA-1
authentication. Any
characters may be used, including spaces, but trailing spaces are truncated.
Apply
Click
Apply
to save your changes back to the ZyWALL.
Cancel
Click
Cancel
to exit this screen without saving.
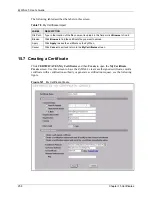
Table 72
VPN Rules (Manual) Edit (continued)
LABEL
DESCRIPTION
Содержание ZyXEL ZyWALL 5
Страница 1: ...ZyWALL 5 Internet Security Appliance User s Guide Version 3 64 3 2005 ...
Страница 2: ......
Страница 26: ...ZyWALL 5 User s Guide 24 ...
Страница 44: ...ZyWALL 5 User s Guide 42 ...
Страница 86: ...ZyWALL 5 User s Guide 84 Chapter 3 Wizard Setup ...
Страница 96: ...ZyWALL 5 User s Guide 94 Chapter 4 LAN Screens ...
Страница 102: ...ZyWALL 5 User s Guide 100 Chapter 5 Bridge Screens ...
Страница 130: ...ZyWALL 5 User s Guide 128 Chapter 7 WAN Screens Figure 45 WAN PPPoE Encapsulation ...
Страница 138: ...ZyWALL 5 User s Guide 136 Chapter 7 WAN Screens Figure 50 Dial Backup Setup ...
Страница 144: ...ZyWALL 5 User s Guide 142 Chapter 7 WAN Screens ...
Страница 152: ...ZyWALL 5 User s Guide 150 Chapter 8 DMZ Screens ...
Страница 174: ...ZyWALL 5 User s Guide 172 Chapter 10 Firewall Screens Figure 68 Creating Editing A Firewall Rule ...
Страница 179: ...ZyWALL 5 User s Guide Chapter 10 Firewall Screens 177 Figure 73 My Service Rule Configuration ...
Страница 220: ...ZyWALL 5 User s Guide 218 Chapter 13 Introduction to IPSec ...
Страница 238: ...ZyWALL 5 User s Guide 236 Chapter 14 VPN Screens Figure 110 VPN Rules IKE Network Policy Edit ...
Страница 261: ...ZyWALL 5 User s Guide Chapter 15 Certificates 259 Figure 122 My Certificate Details ...
Страница 280: ...ZyWALL 5 User s Guide 278 Chapter 16 Authentication Server Figure 133 Local User Database ...
Страница 317: ...ZyWALL 5 User s Guide Chapter 19 Bandwidth Management 315 ...
Страница 318: ...ZyWALL 5 User s Guide 316 Chapter 19 Bandwidth Management ...
Страница 352: ...ZyWALL 5 User s Guide 350 Chapter 21 Remote Management ...
Страница 366: ...ZyWALL 5 User s Guide 364 Chapter 23 Logs Screens Figure 188 Log Settings ...
Страница 389: ...ZyWALL 5 User s Guide Chapter 24 Maintenance 387 Figure 210 Restart Screen ...
Страница 390: ...ZyWALL 5 User s Guide 388 Chapter 24 Maintenance ...
Страница 416: ...ZyWALL 5 User s Guide 414 Chapter 27 WAN and Dial Backup Setup ...
Страница 432: ...ZyWALL 5 User s Guide 430 Chapter 30 DMZ Setup ...
Страница 492: ...ZyWALL 5 User s Guide 490 Chapter 37 System Information Diagnosis ...
Страница 508: ...ZyWALL 5 User s Guide 506 Chapter 38 Firmware and Configuration File Maintenance ...
Страница 520: ...ZyWALL 5 User s Guide 518 Chapter 40 Remote Management ...
Страница 536: ...ZyWALL 5 User s Guide 534 Chapter 42 Troubleshooting Figure 343 Java Sun ...
Страница 564: ...ZyWALL 5 User s Guide 562 Appendix C IP Subnetting ...
Страница 570: ...ZyWALL 5 User s Guide 568 Appendix E PPTP ...
Страница 571: ...ZyWALL 5 User s Guide 569 ...
Страница 572: ...ZyWALL 5 User s Guide 570 ...
Страница 590: ...ZyWALL 5 User s Guide 588 Appendix G Triangle Route ...
Страница 620: ...ZyWALL 5 User s Guide 618 Appendix J Importing Certificates ...
Страница 622: ...ZyWALL 5 User s Guide 620 Appendix K Command Interpreter ...
Страница 628: ...ZyWALL 5 User s Guide 626 Appendix L Firewall Commands ...
Страница 632: ...ZyWALL 5 User s Guide 630 Appendix M NetBIOS Filter Commands ...
Страница 638: ...ZyWALL 5 User s Guide 636 Appendix O Brute Force Password Guessing Protection ...
Страница 660: ...ZyWALL 5 User s Guide 658 Appendix Q Log Descriptions ...