Yoggie Management Console
Advanced Security Settings
60
| Gatekeeper Pico
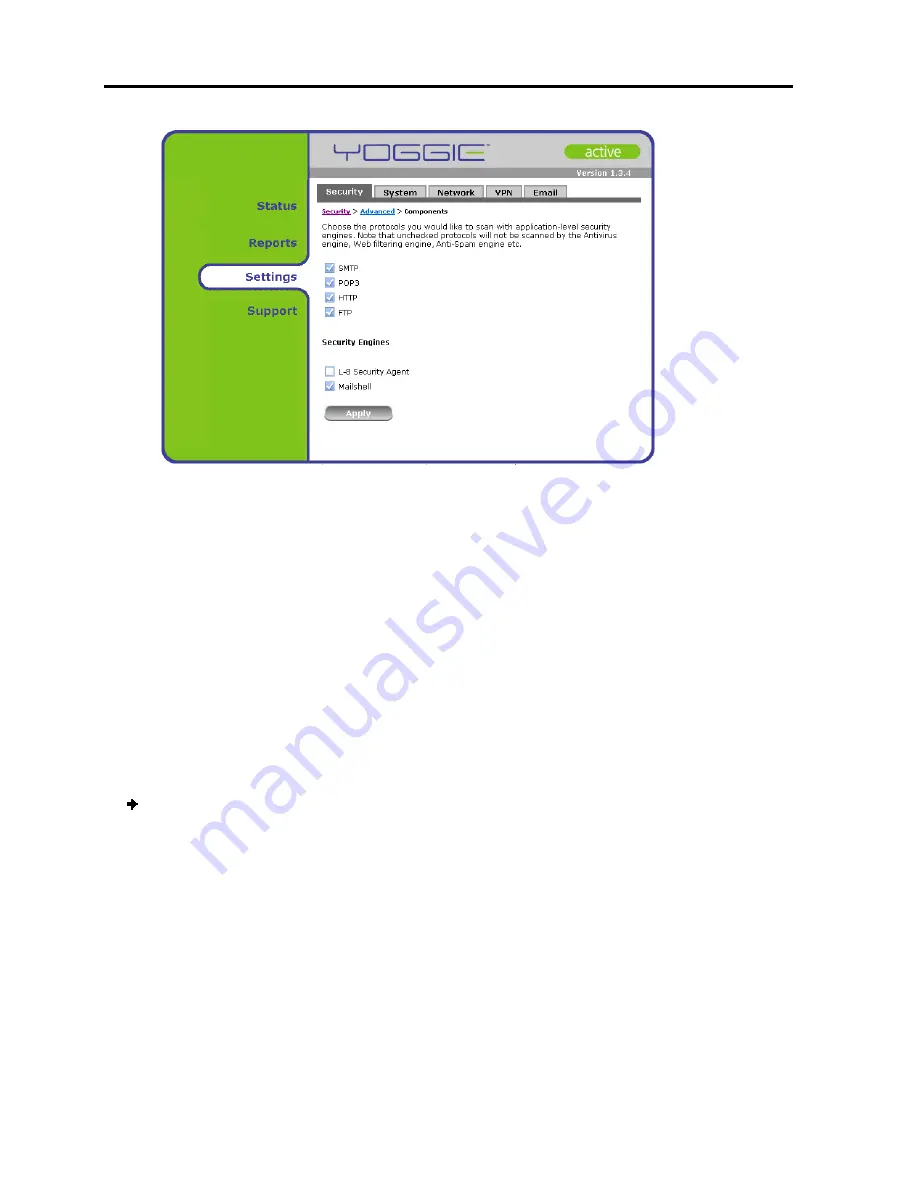
4. Select the checkboxes of the protocols you want Gatekeeper Pico to scan.
5. Select the checkbox of the Security Engine you want Gatekeeper Pico to use:
Select Mailshell if you want to activate spam mail checks.
Select Yoggie`s patent-pending L-8 Security Agent if you wish to activate
Layer-8 protection.
6. Click
Apply
.
Gatekeeper Pico scans the protocols according to the specified settings.
Configuring IDS/IPS
Gatekeeper Pico features IDS/IPS protection. In this advanced configuration option
you can specify the security policies for each activity.
To configure IDS/IPS protection:
1. Click
Settings
in the
Navigation
pane of the Management Console.
The
Security
tab appears in the
Display
pane.
2. Click
Advanced
.
3. Click
IDS/IPS
.
The
IDS/IPS Policy
screen appears.
Содержание GATEKEEPER PICO
Страница 1: ...www yoggie com...


























