_______________________________________________________________________________________________________
_______________________________________________________________________________________________________
© Virtual Access 2018
GW2020 Series User Manual
Issue: 2.1
Page 306 of 423
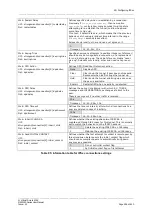
Web: Local Port
UCI: strongswan.@connection[X].localport
Opt: localport
Restricts the connection to a single port on the local side.
Web: Remote Protocol
UCI:
strongswan.@connection[X].remoteproto
Opt:remoteproto
Restricts the connection to a single protocol on the remote side.
Web: Remote Port
UCI:
strongswan.@connection[X].remoteport
Opt: remoteport
Restricts the connection to a single port on the remote side.
Web: Authby
UCI: strongswan.@connection[X].authby
Opt: authby
Defines how the two secure gateways should authenticate.
Note: using aggressive mode along with PSK authentication is
unsecure and should be avoided.
Pubkey
For public key signatures.
Rsasig
For RSA digital signatures.
ecdsasig
For Elliptic Curve DSA signatures.
Psk
Using a preshared key.
xauthrsasig Enables eXtended Authentication (XAuth) with
addition to RSA signatures.
xauthpsk
Using extended authentication and preshared
key.
never
Can be used if negotiation is never to be
attempted or accepted (shunt connections).
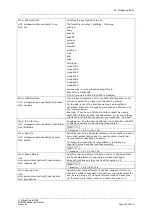
Web: XAuth Identity
UCI:
strongswan.@connection[X].xauth_identity
Opt: xauth_identity
Defines Xauth ID.
Web: IKE Algorithm
UCI: strongswan.@connection[X].ike
Opt: ike
Specifies the IKE algorithm to use.
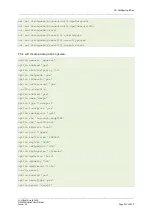
The format is: encAlgo | authAlgo | DHGroup:
encAlgo:
3des
aes128
aes256
serpent
twofish
blowfish
authAlgo:
md5
sha
sha2
DHGroup:
modp1024
modp1536
modp2048
modp3072
modp4096
modp6144
modp8192
For example, a valid IKE algorithm is: aes128-sha-modp1536.