_______________________________________________________________________________________________________
_______________________________________________________________________________________________________
© Virtual Access 2018
GW2020 Series User Manual
Issue: 2.1
Page 296 of 423
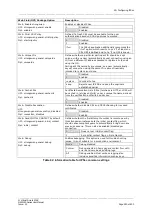
Web: Restart Delay
UCI: strongswan.@connection[X].restartdelay
Opt: restartdelay
Defines specific delay when re-establishing a connection.
Previously if
close_action=restart
, then new option
restartdelay
controls how many seconds it waits before
attempting to re-establish the tunnel (to allow head-end
some time to tidy up).
If not set, it defaults to zero, which means that the previous
behaviour of choosing a random time interval in the range
0..
RekeyMargin
seconds takes effect.
Relevant only locally, other end need not agree on it.
0
Timespec 1d, 2h, 9m, 10s.
Web: Keying Tries
UCI: strongswan.@connection[X].keyringtries
Opt: keyringtries
Specifies how many attempts (a positive integer or %forever)
should be made to negotiate a connection, or a replacement
for one, before giving up. The value %forever means 'never
give up'. Relevant only locally, other end need not agree on
it.
Web: DPD Action
UCI: strongswan.@connection[X].dpdaction
Opt: dpdaction
Defines DPD (Dead Peer Detection) action.
None
Disables DPD.
Clear
Clear down the tunnel if peer does not respond.
Reconnect when traffic brings the tunnel up.
Hold
Clear down the tunnel and bring up as soon as
the peer is available.
Restart
Restarts DPD when no activity is detected.
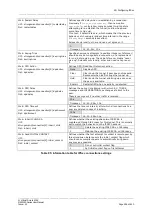
Web: DPD Delay
UCI: strongswan.@connection[X].dpddelay
Opt: dpddelay
Defines the period time interval with which R_U_THERE
messages and INFORMATIONAL exchanges are sent to the
peer.
These are only sent if no other traffic is received.
30s
Timespec 1d, 2h, 25m, 10s.
Web: DPD Timeout
UCI: strongswan.@connection[X].dpdtimeout
Opt: dpdtimeout
Defines the timeout interval, after which all connections to a
peer are deleted in case of inactivity.
150s
Timespec 1d, 2h, 25m, 10s.
Web: Inherit CHILD SA
UCI:
strongswan.@connection[X].inherit_child
Opt: inherit_child
Defines whether the existing phase two IPSEC SA is
maintained through IKE rekey for this tunnel. This is normally
set to match the behaviour on the IPSEC headend.
0
Delete the existing IPSEC SA on IKE rekey
1
Maintain the existing IPSEC SA on IKE rekey
Web: Send INITIAL CONTACT
UCI:
strongswan.@connection[X].initial_contact
Opt: initial_contact
Defines whether the first attempt to contact a remote peer by
this strongswan instance sets the initial_contact flag which
should cause compliant peers to automatically bring down
any previous sessions.
0
Do not set initial contact flag
1
Set initial contact flag on first attempt
Table 95: Information table for IPSec connections settings