_______________________________________________________________________________________________________
_______________________________________________________________________________________________________
© Virtual Access 2018
GW2020 Series User Manual
Issue: 2.1
Page 282 of 423
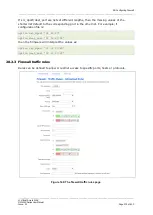
28.7.2
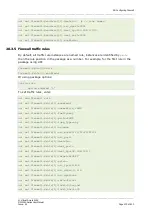
Forwarding ports (destination NAT/DNAT)
This example forwards http, but not HTTPS, traffic to the web server running on
192.168.1.10:
config redirect
option src wan
option src_dport 80
option proto tcp
option dest_ip 192.168.1.10
The next example forwards one arbitrary port that you define to a box running SSH
behind the firewall in a more secure manner because it is not using default port 22.
config 'redirect'
option 'name' 'ssh'
option 'src' 'wan'
option 'proto' 'tcpudp'
option 'src_dport' '5555'
option 'dest_ip' '192.168.1.100'
option 'dest_port' '22'
option 'target' 'DNAT'
option 'dest' 'lan'
28.7.3
Source NAT (SNAT)
Source NAT changes an outgoing packet destined for the system so that is looks as
though the system is the source of the packet.
Define source NAT for UDP and TCP traffic directed to port 123 originating from the host
with the IP address 10.55.34.85. The source address is rewritten to 63.240.161.99.
config redirect
option src lan
option dest wan
option src_ip 10.55.34.85
option src_dip 63.240.161.99
option dest_port 123
option target SNAT
When used alone, Source NAT is used to restrict a computer's access to the internet, but
allows it to access a few services by manually forwarding what appear to be a few local