78 Populating the topology database
Managing the topology tree
Managing the topology tree
To configure Symantec Network Security, first populate the topology database
to provide key information about your network. Collect this key information
described in the
Gathering information
section. After you add this information
to the database, you can edit it at any time by modifying the tree, and adjust to
new information, network reorganization, or other changes to the network.
This section describes how to edit and delete object information, reverse or save
your changes, refresh your view, and back up your topology database, as follows:
■
Viewing auto-generated objects
■
Viewing node details
■
Viewing node status
■
Adding objects for the first time
■
Editing objects
■
Deleting objects
■
Reverting changes
■
Saving changes
■
Forcing nodes to synchronize
■
Backing up
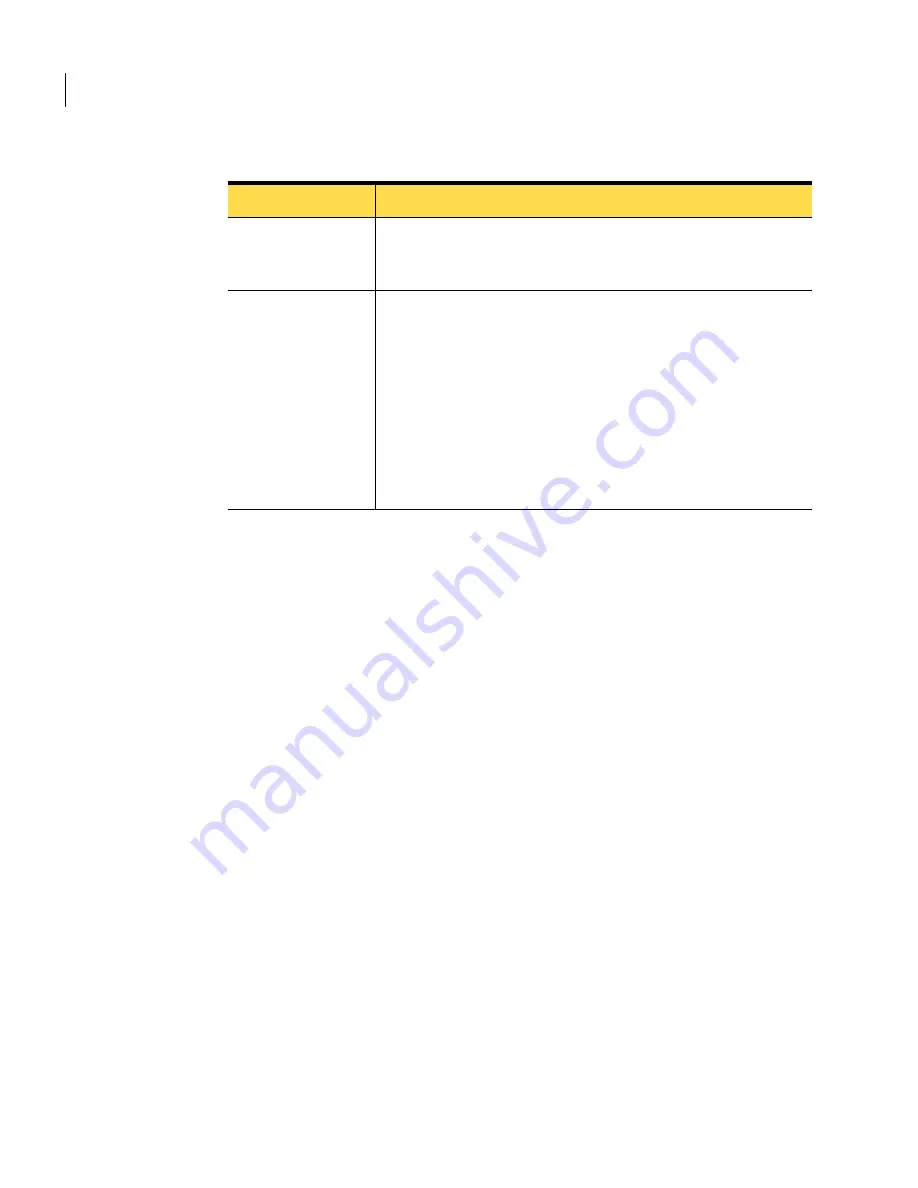
Interface name
For each interface in the topology tree, follow the naming
convention of the manufacturer for that interface, such as
qfe0
or
fa/0
.
Synchronization
passphrases
For some objects in the topology tree, provide a unique
synchronization passphrase between 6 and 64 characters,
inclusive. This enables nodes to communicate securely during
database synchronization and cross-node event correlation. Make
a note of the synchronization passphrase so you can supply it
when you physically install the slave node.
Note:
You cannot edit this passphrase. If you fail to provide, or
provide an erroneous passphrase when you add the slave node,
you must delete the node, create a new one, and assign a new
synchronization passphrase to it.
Table 4-1
Information to gather
Field
Description
Содержание 10521146 - Network Security 7120
Страница 1: ...Symantec Network Security Administration Guide...
Страница 12: ...12 Contents Index...
Страница 14: ...14...
Страница 70: ...70...
Страница 110: ...110 Populating the topology database Adding nodes and objects...
Страница 158: ...158 Responding Managing flow alert rules...
Страница 188: ...188...
Страница 242: ...242 Reporting Playing recorded traffic...
Страница 268: ...268 Managing log files Exporting data...
Страница 316: ...316 Advanced configuration Configuring advanced parameters...
Страница 317: ...Part IV Appendices The following appendices provide additional reference information User groups reference SQL reference...
Страница 318: ...318...
Страница 338: ...338 SQL reference Using MySQL tables...
Страница 366: ...366 Glossary...
Страница 392: ...392 Index...









































