ULTRACONSOLE REMOTE 2 INSTALLATION AND OPERATIONS MANUAL
9
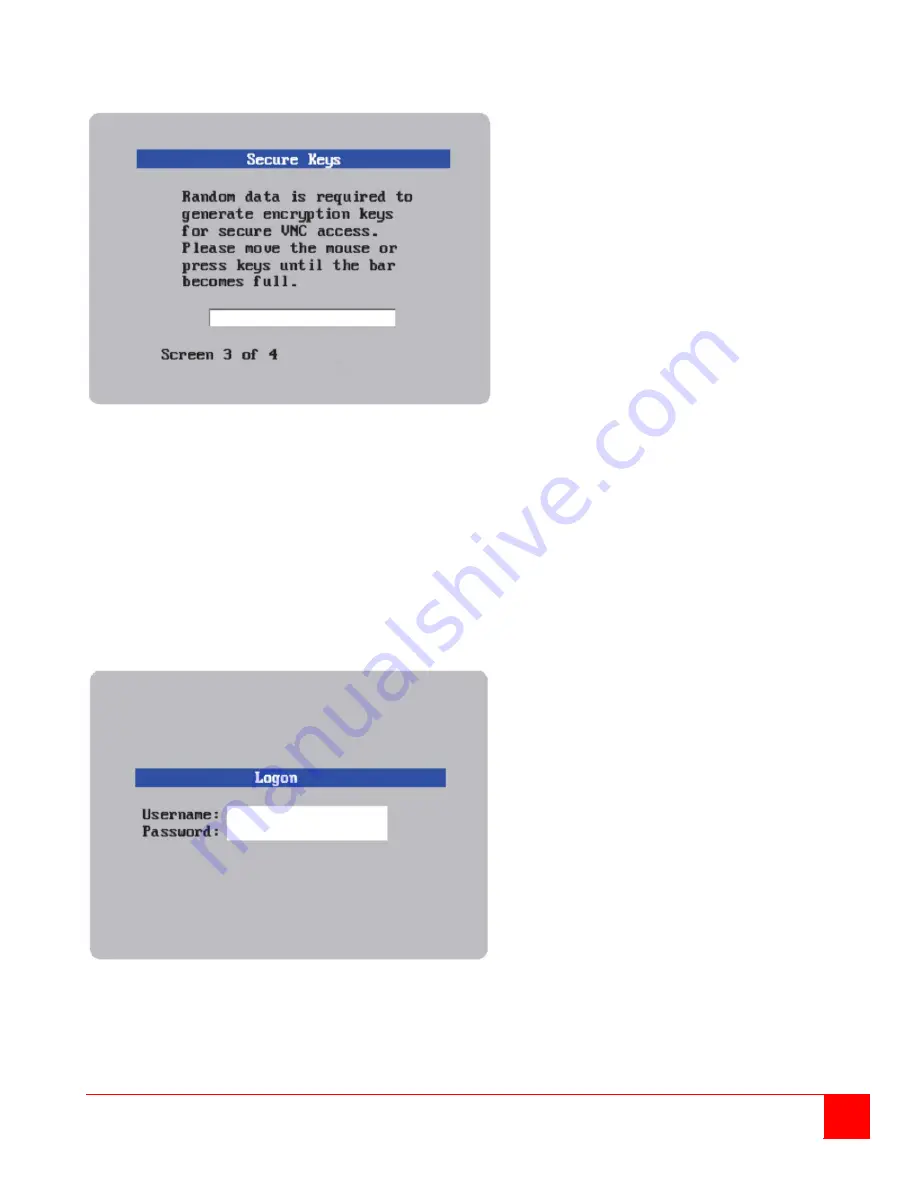
Screen #3 is a Secure Keys screen that will display after the network information has been entered.
Figure 5. Secure Keys Encryption
This screen uses mouse movements and keyboard inputs to create random data. This unpredictable information is
then combined with several other factors to develop the basis of the encryption keys that are used to establish
secure remote links.
With every mouse move and key press the single dash will move across the progression bar (unless the same key is
pressed repeatedly). Periodically, a new star character will be added to the bar as the random data are accepted as
part of the new encryption key. When the bar is full, the final encryption keys for your UltraConsole Remote 2 will be
created – this process takes roughly 30 to 40 seconds.
Once the secure key has been calculated, the UltraConsole Remote 2 will restart and present a standard logon
screen as shown below.
Figure 6. Logon screen
At this stage the username is still ‘
admin
’ but the password will be whatever you entered on the Unit Configuration
setup screen. Once the username and password has been validated, the screen should now show the host computer
video.
Содержание UCR-1R1X16U/2
Страница 2: ......
Страница 4: ......
Страница 67: ......
Страница 68: ...10707 Stancliff Road Phone 281 933 7673 Houston Texas 77099 www rose com ...
















































