IPv4 Access Control Lists (ACLs)
Overview
General Steps for Planning and Configuring ACLs
1. Identify the ACL application to apply. As part of this step, determine the
best points at which to apply specific ACL controls. For example, you can
improve network performance by filtering unwanted IPv4 traffic at the
edge of the network instead of in the core. Also, on the switch itself, you
can improve performance by filtering unwanted IPv4 traffic where it is
inbound to the switch instead of outbound.
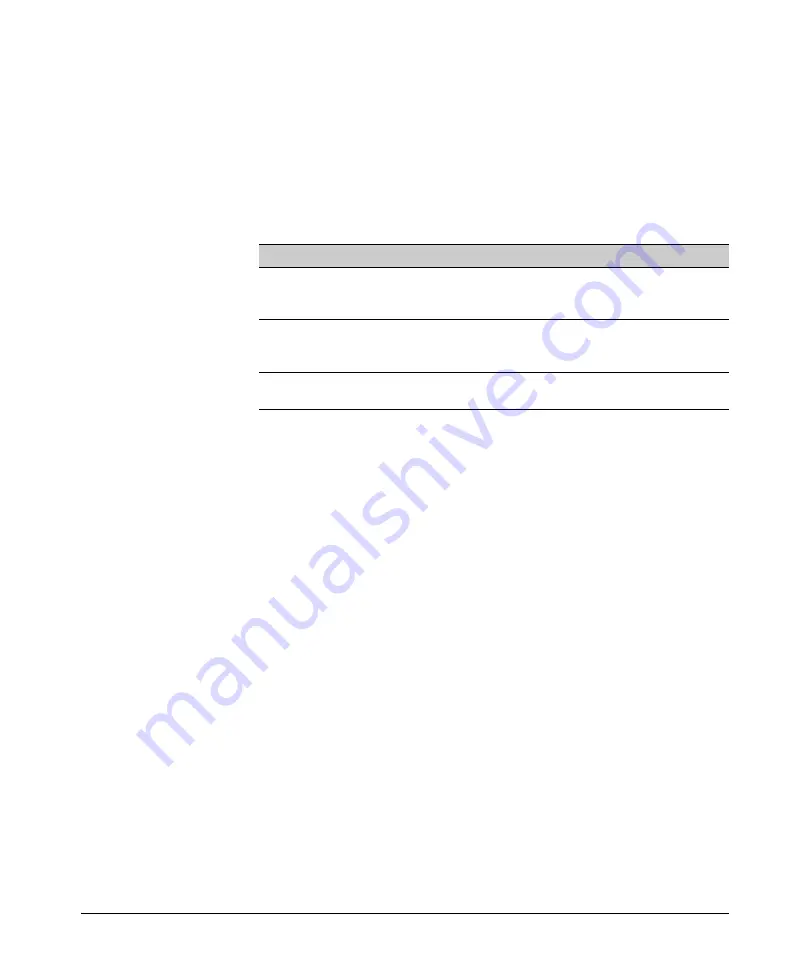
Traffic Source
ACL Application
IPv4 traffic from a specific, authenticated dynamic port ACL (RADIUS-assigned ACL)
client
for inbound IP traffic from an authenticated
client on a port*
IPv4 traffic entering the switch on a
static port ACL (static-port assigned) for
specific port
any inbound IPv4 traffic on a port from any
source
*For more on this option, refer to chapter 6, “Configuring RADIUS Server Support for
Switch Services”, and also to the documentation for your RADIUS server.)
2. Identify the traffic types to filter.
•
The SA and/or the DA of traffic you want to permit or deny. This can
be a single host, a group of hosts, a subnet, or all hosts.
•
Traffic of a specific IPv4 protocol type (0-255)
•
Any TCP traffic (only) for a specific TCP port or range of ports,
including optional control of connection traffic based on whether the
initial request should be allowed
•
All UDP traffic or UDP traffic for a specific UDP port
•
All ICMP traffic or ICMP traffic of a specific type and code
•
All IGMP traffic or IGMP traffic of a specific type
•
Any of the above with specific precedence and/or ToS settings
3. Design the ACLs for the control points (interfaces) you have selected.
Where you are using explicit “deny” ACEs, you can optionally use the ACL
logging feature for notification that the switch is denying unwanted
packets.
4. Configure the ACLs on the selected switches.
5. Assign the ACLs to the interfaces you want to filter, using the ACL
application appropriate for each assignment. (For RADIUS-assigned
ACLs, refer to the Note in the table in step 1 on page 9-18.)
6. Test for desired results.
9-18
Содержание PROCURVE 2910AL
Страница 1: ...Access Security Guide ProCurve Switches W 14 03 2910al www procurve com ...
Страница 2: ......
Страница 3: ...HP ProCurve 2910al Switch February 2009 W 14 03 Access Security Guide ...
Страница 84: ...Configuring Username and Password Security Front Panel Security 2 36 ...
Страница 156: ...TACACS Authentication Operating Notes 4 30 ...
Страница 288: ...Configuring Secure Socket Layer SSL Common Errors in SSL setup 8 22 ...
Страница 416: ...Configuring Advanced Threat Protection Using the Instrumentation Monitor 10 28 ...
Страница 516: ...Configuring Port Based and User Based Access Control 802 1X Messages Related to 802 1X Operation 12 76 ...
Страница 527: ...Configuring and Monitoring Port Security Port Security Figure 13 4 Examples of Show Mac Address Outputs 13 11 ...
Страница 572: ...Using Authorized IP Managers Operating Notes 14 14 ...
Страница 592: ...12 Index ...
Страница 593: ......
Страница 594: ... Copyright 2009 Hewlett Packard Development Company L P February 2009 Manual Part Number 5992 5439 ...
















































