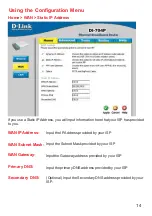
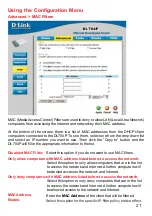
6
Features & Benefits
continued
Access Control supported
Allows you to assign different access rights for different users
Packet filter supported
Packet Filter
allows you to control access to a network by analyzing the
incoming and outgoing packets and letting them pass or halting them
based on the IP address of the source and destination.
Virtual Server supported
Enables you to expose WWW, FTP and other services on your LAN to be
accessible to Internet users.
User-Definable Application Sensing Tunnel
User can define the attributes to support special applications requiring
multiple connections, like Internet gaming, video conferencing, Internet
telephony and so on. The DI-704P can sense the application type and
open a multi-port tunnel for it.
DMZ Host supported
Allows a networked computer to be fully exposed to the Internet; this
function is used when the special “application-sensing tunnel feature” is
insufficient to allow an application to function correctly
Introduction to Broadband
Router Technology
A router is a device that forwards data packets from a source to a destination. Routers
forward data packets using IP addresses and not a MAC address. A router will forward
data from the Internet to a particular computer on your LAN.
The information that makes up the Internet gets moved around using routers. When
you click on a link on a web page, you send a request to a server to show you the next
page. The information that is sent and received from your computer is moved from your
computer to the server using routers. A router also determines the best route that your
information should follow to ensure that the information is delivered properly.
A router controls the amount of data that is sent through your network by eliminating
information that should not be there. This provides security for the computers con-
nected to your router, because computers from the outside cannot access or send
information directly to any computer on your network. The router determines which
computer the information should be forwarded to and sends it. If the information is not
intended for any computer on your network, the data is discarded. This keeps any
unwanted or harmful information from accessing or damaging your network.