137
APPENDIX C: FEATURES AND SPECIFICATIONS
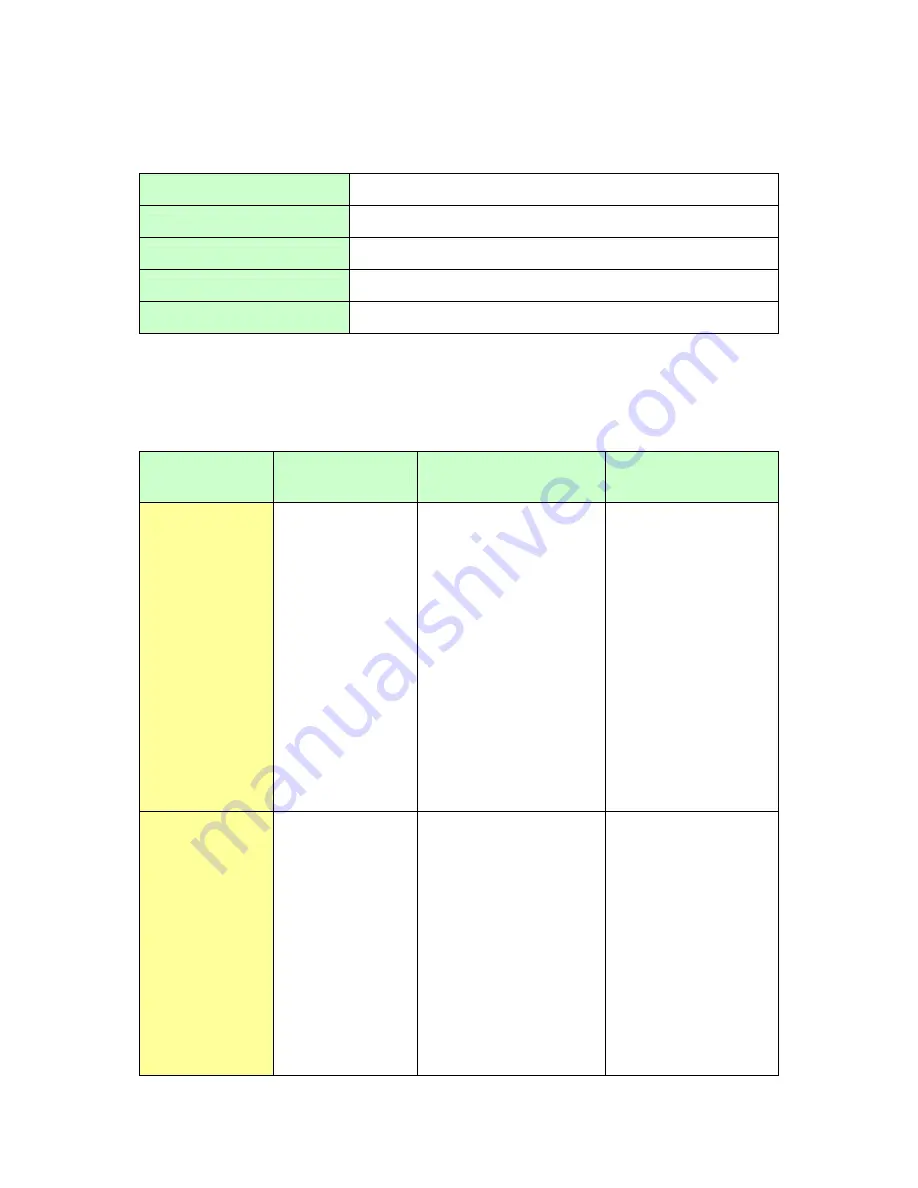
Hardware Specification
Ethernet
2 x 10/100 M auto-sensing auto-crossing with frog light
Other port
RS232(9 pin)
LCD Module
Blue background with white light LCD Panel
Power
AC LINE 100-240V AC 50-60Hz 0.8A MAX
Dimension (L*D*H, mm)
440mm * 250mm * 44mm
Features Specification
Application Detection / Prevention / Management
Application
Class
Application Type
Application Name
Control Points
1. Message
Exchange
*Instant
Messengers (IM)
1. MSN
2. Yahoo
Messenger
3. ICQ
4. AIM
5. QQ
6. IChat
(MAC)
7. Odigo
8. Trillian
1. Login
2. Send/Receive
Message
3. Send
File
4. File
Type/Name/Size
5. Receive
File
6. VoIP
Establishment
7. Video
Establishment
8. White
Board
Establishment
2. Internet
File
Sharing
*Peer-to-Peer
(P2P)
1. EzPeer
2. eDonkey
3. Skype
4. eMule
5. Kazaa
6. Limwire
7. BitTorrent
8. Grokster
9. Gnutella
10. Shareaza
1. Connection
Establishment
Содержание DFL-M510
Страница 2: ......
Страница 6: ...iv ...
Страница 60: ...51 When the settings are processed the following screen appears 5 Click OK to finish ...
Страница 63: ...54 PARAMETER TAB Click the Parameter tab The following screen appears This tab defines management parameters ...
Страница 80: ...71 3 Enter a file name and click Save 4 Click OK to confirm the export 5 Click OK to continue ...
Страница 95: ...86 5 Under Group Host select PM and click Apply ...
Страница 99: ...90 3 Input a pattern named Streaming 1 with category Streaming Media and TCP port 3001 4 Click Save ...
Страница 101: ...92 3 Input a rule name Web Chat 1 with category Web Control and servers 140 126 21 4 4 Click Save ...
Страница 104: ...95 2 Under Popup Message to User click Add 3 Type a description and the content of the message and click OK ...






















