9-32
Cisco ASA Series Firewall CLI Configuration Guide
Chapter 9 Network Address Translation (NAT)
Static NAT
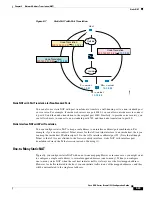
The following figure shows a typical many-to-few static NAT scenario.
Figure 9-11
Many-to-Few Static NAT
Instead of using a static rule this way, we suggest that you create a one-to-one rule for the traffic that
needs bidirectional initiation, and then create a dynamic rule for the rest of your addresses.
Configure Static Network Object NAT or Static NAT-with-Port-Translation
This section describes how to configure a static NAT rule using network object NAT.
Procedure
Step 1
(Optional.) Create a network object (
object network
command), or a network object group
(
object-group network
command), for the mapped addresses.
•
Instead of using an object, you can configure an inline address or specify the interface address (for
static NAT-with-port-translation).
•
If you use an object, the object or group can contain a host, range, or subnet.
Step 2
Create or edit the network object for which you want to configure NAT.
object network
obj_name
Example
hostname(config)# object network my-host-obj1
Step 3
(Skip when editing an object that has the right address.) Define the real IPv4 or IPv6 addresses that you
want to translate.
•
host
{
IPv4_address
|
IPv6_address
}—The IPv4 or IPv6 address of a single host. For example,
10.1.1.1 or 2001:DB8::0DB8:800:200C:417A.
•
subnet
{
IPv4_address
IPv4_mask
|
IPv6_address
/
IPv6_prefix
}—The address of a network. For
IPv4 subnets, include the mask after a space, for example, 10.0.0.0 255.0.0.0. For IPv6, include the
address and prefix as a single unit (no spaces), such as 2001:DB8:0:CD30::/60.
•
range
start_address
end_address
—A range of addresses. You can specify IPv4 or IPv6 ranges. Do
not include masks or prefixes.
Example
hostname(config-network-object)# subnet 10.2.1.0 255.255.255.0
Step 4
Configure
static NAT
for the object IP addresses. You can only define a single NAT rule for a given
object.
10.1.2.27
209.165.201.3
In
s
ide
O
u
t
s
ide
10.1.2.28
209.165.201.4
10.1.2.29
209.165.201.3
10.1.2.30
209.165.201.4
10.1.2.31
209.165.201.3
S
ec
u
rity
Appli
a
nce
24
8
770
Содержание ASA 5508-X
Страница 11: ...P A R T 1 Access Control ...
Страница 12: ......
Страница 60: ...4 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 4 Access Rules History for Access Rules ...
Страница 157: ...P A R T 2 Network Address Translation ...
Страница 158: ......
Страница 204: ...9 46 Cisco ASA Series Firewall CLI Configuration Guide Chapter 9 Network Address Translation NAT History for NAT ...
Страница 232: ...10 28 Cisco ASA Series Firewall CLI Configuration Guide Chapter 10 NAT Examples and Reference DNS and NAT ...
Страница 233: ...P A R T 3 Service Policies and Application Inspection ...
Страница 234: ......
Страница 379: ...P A R T 4 Connection Management and Threat Detection ...
Страница 380: ......
Страница 400: ...16 20 Cisco ASA Series Firewall CLI Configuration Guide Chapter 16 Connection Settings History for Connection Settings ...
Страница 414: ...17 14 Cisco ASA Series Firewall CLI Configuration Guide Chapter 17 Quality of Service History for QoS ...