ClearPass Guest 3.9 | Deployment Guide
Administrator Tasks |
411
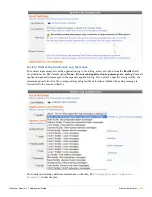
System Log
The system log viewer available on the
Support > System Logs
page displays messages that have been
generated from multiple different sources:
Application Logs
—messages generated by the ClearPass Guest application.
HTTP Logs
—messages generated by the Apache Web Server.
RADIUS Logs
—messages generated by the RADIUS server during authentication, authorization or
accounting.
System Logs
—messages generated by the system and various internal processes within it. Depending
on the plugins you have installed, additional message sources may also be included in the system log
viewer.
The information shown in the table is a summary of the log message. Click a log entry in the table to view
the details of the log message.
Use the paging control at the bottom of the list to jump forwards or backwards by one page, or to the first or
last page of the list. You can also click an individual page number to jump directly to that page.
Use the
Refresh
link, or the Auto-refresh drop-down list, to keep the displayed log messages up to date.
Filtering the System Log
Use the Keywords field to perform a keyword search. Only the log messages that match the keywords
entered are displayed. Click the
Clear Filter
link to restore the default view.
Содержание ClearPass Guest 3.9
Страница 1: ...ClearPass Guest 3 9 Deployment Guide ...
Страница 32: ...32 Management Overview ClearPass Guest 3 9 Deployment Guide ...
Страница 178: ...178 RADIUS Services ClearPass Guest 3 9 Deployment Guide ...
Страница 316: ...316 Guest Management ClearPass Guest 3 9 Deployment Guide ...
Страница 328: ...328 Report Management ClearPass Guest 3 9 Deployment Guide Figure 46 Components of the Report Editor Report Type ...
Страница 410: ...410 Administrator Tasks ClearPass Guest 3 9 Deployment Guide ...
Страница 414: ...414 Administrator Tasks ClearPass Guest 3 9 Deployment Guide ...
Страница 423: ...ClearPass Guest 3 9 Deployment Guide Hotspot Manager 423 ...
Страница 440: ...440 High Availability Services ClearPass Guest 3 9 Deployment Guide ...
Страница 518: ...518 Index ClearPass Guest 3 9 Deployment Guide ...