Copyright © Acronis, Inc., 2000-2010
367
Dynamic disk
A hard disk managed by Logical Disk Manager (LDM) that is available in Windows starting with
Windows 2000. LDM helps flexibly allocate volumes on a storage device for better fault tolerance,
better performance or larger volume size.
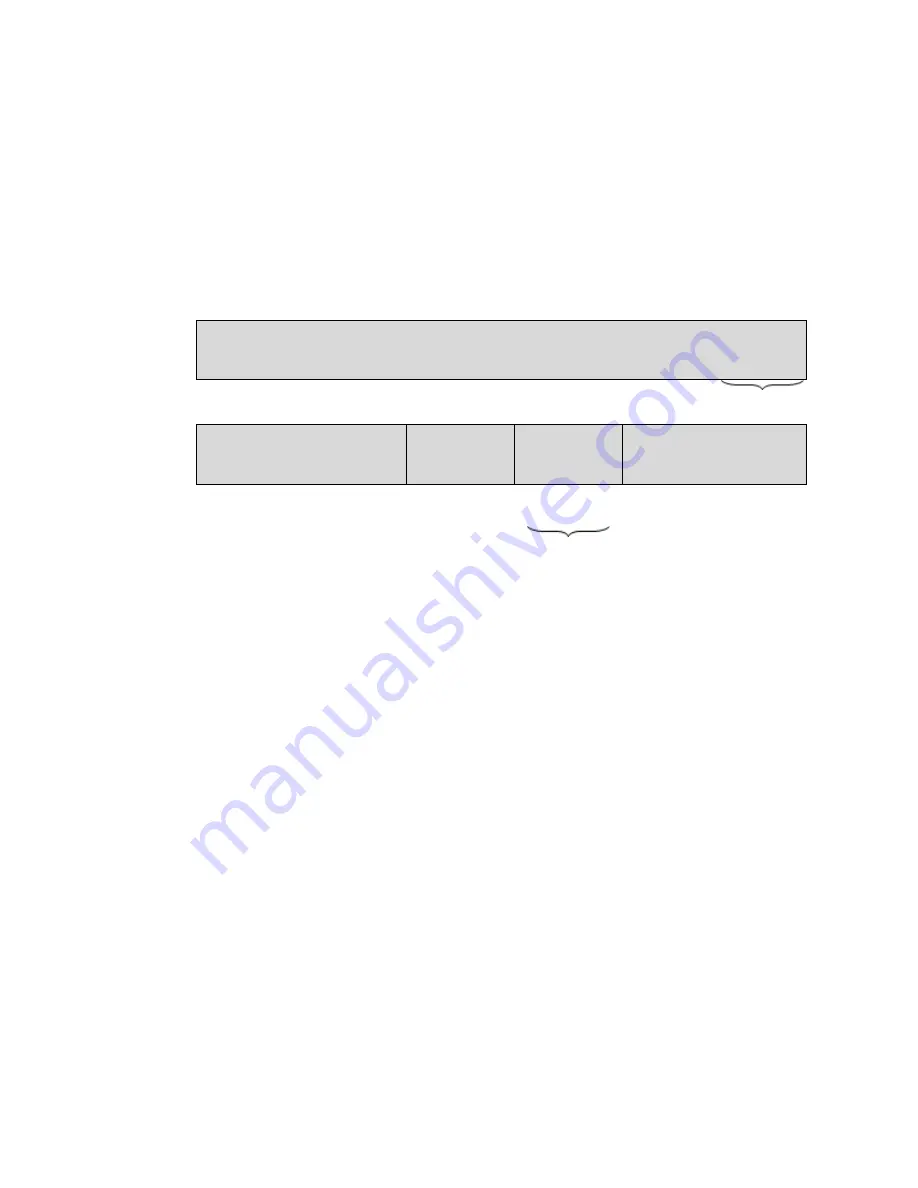
A dynamic disk can use either the master boot record (MBR) or GUID partition table (GPT) partition
style. In addition to MBR or GPT, each dynamic disk has a hidden database where the LDM stores the
dynamic volumes' configuration. Each dynamic disk holds the complete information about all
dynamic volumes existing in the disk group which makes for better storage reliability. The database
occupies the last 1MB of an MBR disk. On a GPT disk, Windows creates the dedicated LDM Metadata
partition, taking space from the Microsoft Reserved Partition (MSR.)
Disk 1
MBR
LDM
database
1 MB
Disk 2
Protec-
tive
MBR
GPT
Microsoft
Reserved
Partition (MSR)
LDM
database
GPT
LDM Metadata
partition
1 MB
Dynamic disks organized on MBR (Disk 1) and GPT (Disk 2) disks.
For more information about dynamic disks please refer to the following Microsoft knowledge base
articles:
Disk Management (Windows XP Professional Resource Kit) http://technet.microsoft.com/en-
us/library/bb457110.aspx
816307 Best practices for using dynamic disks on Windows Server 2003-based computers
http://support.microsoft.com/kb/816307
Dynamic group
A group of machines (p. 369) which is populated automatically by the management server (p. 370)
according to membership criteria specified by the administrator. Acronis Backup & Recovery 10
offers the following membership criteria:
Operating system
Active Directory organization unit
IP address range.
A machine remains in a dynamic group as long as the machine meets the group's criteria. The
machine is removed from the group automatically as soon as
the machine's properties change so that the machine does not meet the criteria anymore OR
the administrator changes the criteria so that the machine does not meet them anymore.
There is no way to remove a machine from a dynamic group manually except for deleting the
machine from the management server.






























