SNMP and SMT Proxy Agents
3-7
SNMP and SMT
Proxy Agents
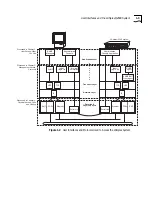
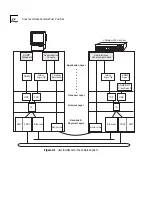
A proxy agent acts as a management gateway. It converts requests and
event reports from one protocol and object format to another protocol and
object format.
Your LANplex system contains a proxy agent that translates between SNMP
and FDDI SMT. It allows a network management station that is not
necessarily connected directly to an FDDI LAN to manage FDDI end-stations
on that LAN, even if the FDDI end-stations do not support SNMP. For all the
stations in that FDDI LAN to be managed, only one LANplex proxy agent
needs to be active on each FDDI LAN within your network.
Содержание LANPLEX 2500
Страница 1: ...LANPLEX 2500 OPERATION GUIDE Part No 801 00344 000 Published November 1996 Revision 03...
Страница 14: ......
Страница 18: ...1 4 CHAPTER 1 LANPLEX MANAGEMENT AND ADMINISTRATION OVERVIEW...
Страница 78: ...III Chapter 9 FDDI Overview and Implementation Chapter 10 FDDI Networks FDDI TECHNOLOGY...
Страница 97: ...IV Chapter 11 ATM Networks ATM TECHNOLOGY...
Страница 116: ...V Appendix A SNMP MIB Support Appendix B Technical Support APPENDIXES...