Gateway Installation and Support Guide
6
Configuring Wireless Adapters
2Wire Wireless Adapters
If you use a 2Wire wireless adapter (PCI, PC card, or USB adapter) for wireless networking, the gateway
installation software automatically configures it to communicate with the gateway during setup.
Non-2Wire Wireless Adapters
If you are NOT using a 2Wire wireless adapter, you will need to manually configure your adapter of choice to
communicate with the gateway using the information below.
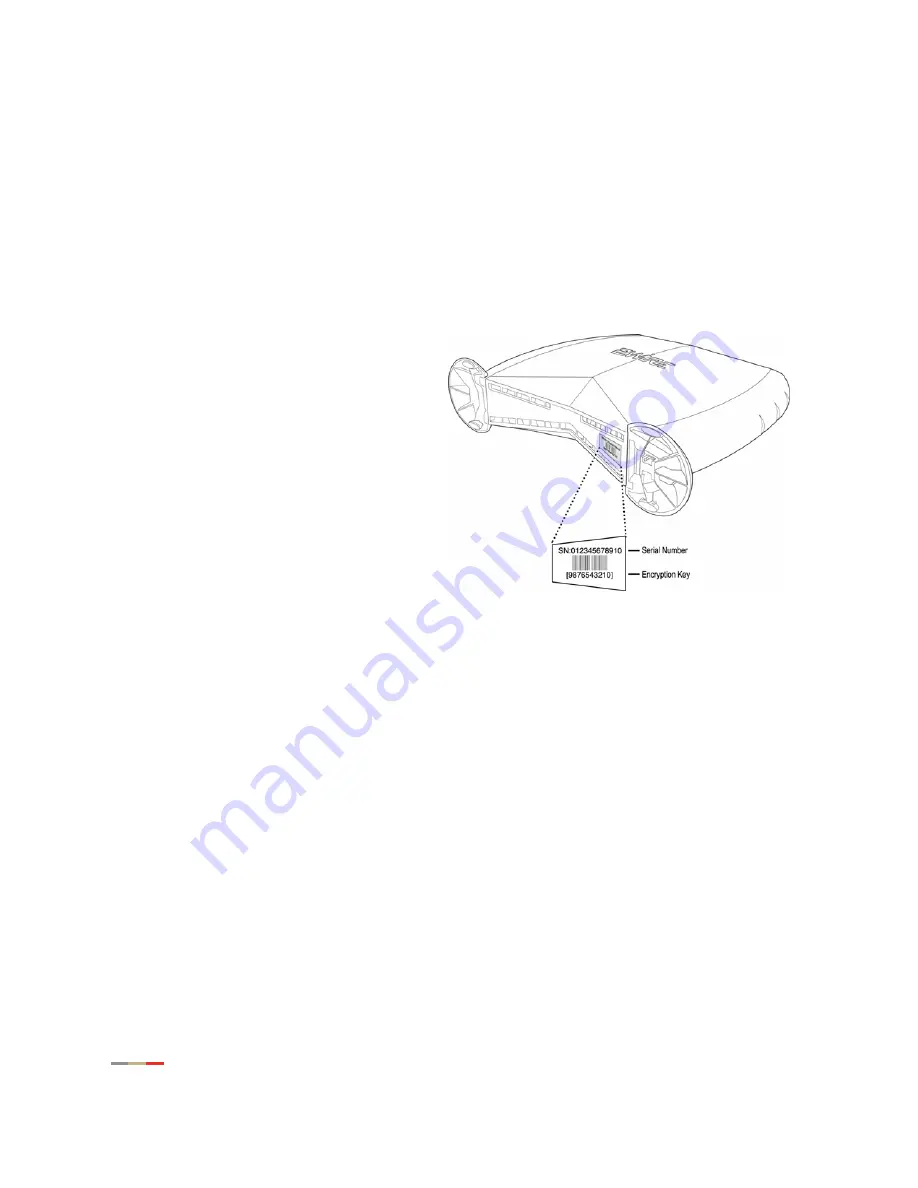
Locating the Serial Number and Wireless
Encryption Key
Your gateway is configured with unique security
parameters that must be configured into your
wireless adapter: the serial number and a
default 64-bit WEP wireless encryption key. You
will find these two important pieces of
information on the bottom of your gateway.
Adapter Configuration
After you have located the serial number and
wireless encryption key, configure your wireless
adapter according to instructions provided with
that product.
1.
Set the network type to Infrastructure. Refer
to your wireless adapter documentation for instructions on editing the adapter's network profile. Your
wireless adapter should be configured to operate with an access point or residential gateway. This
mode of operation is typically enabled by setting network type to Infrastructure.
2.
Set the wireless network name. The wireless network name of your gateway is 2WIRE in all capital
letters, followed by the last three digits of the gateway serial number located on the bottom of your
gateway. For example, if the last three digits of your gateway serial number are 102, your gateway
network name would be
2WIRE102
.
The wireless network name is sometimes referred to as the Network Name, SSID, ESS ID, or Wireless
LAN ID.
3.
Enable wireless security. Your gateway is pre-configured to take advantage of wireless security.
Referring to the instructions provided with your wireless adapter, enable wireless security.
The default wireless security used by the gateway is sometimes referred to as WEP (wired equivalent
privacy), 64-bit encryption, or 40-bit encryption.


















