Secured Content Delivery
228
SWRU455A – February 2017 – Revised March 2017
Copyright © 2017, Texas Instruments Incorporated
Crypto Utilities
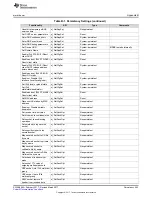
Table 16-2. Common Errors (continued)
Error Code
Value
Comments
SL_ERROR_NETUTIL_CRYPTO_EMPTY_DB_ENTRY
-12296
The provided index points to an empty
database entry.
SL_ERROR_NETUTIL_CRYPTO_NON_TEMPORARY_KEY -12297
The host application is trying to perform
an operation related to temporary keys,
but the provided index does not contain a
temporary key.
SL_ERROR_NETUTIL_CRYPTO_DB_ENTRY_NOT_FREE
-12298
The provided index points to a nonempty
database entry (while the requested
operation requires the entry to be empty).
SL_ERROR_NETUTIL_CRYPTO_CORRUPTED_DB_FILE
-12299
The file that stores the database on the
filesystem (for persistency) has been
corrupted.
16.2 Secured Content Delivery
The secure content delivery lets the user program a secured file encrypted by a remote device and
decrypted inside the NWP, while the private key used for the process remains inside the SimpleLink Wi-Fi
networking subsystem alone with no access from the host. This ability lets the user transfer a file to the
system on any unsecured tunnel.
16.2.1 Process Flow
1. Retrieve a temporary, nonpersistent ECC public key using the NetUtils APIs described in
.
2. Send the public key to the application remote server.
3. Receive the encrypted file.
4. Open a new file with a special flag, indicating secure content delivery is about to be written:
secAccessFlags = SL_FS_FILE_MODE_OPEN_CREATE(fpInSize,SL_FS_FILE_DOWNLOAD_SECURED_CONTENT);
fileHande = sl_FsOpen("sec_cont1.txt",secAccessFlags,NULL);
if
(0 > fileHande)
{
/* error */
}
5. Write the file sequentially and by order – the offset attribute in the sl_FsWrite has no meaning
regarding a secured content delivery write, and is ignored.
6. Close the file using the sl_FsClose API.
At the end of this process, the file is saved on the SFLASH, and encrypted as a normal secured file with a
different key and method than the file used for the reception process.