User’s Manual
Synaccess Networks, Inc.
www.synaccess-net.com
(760) 930 – 0473 Page 5 of 46
1 System Description
1.1 System Key Features:
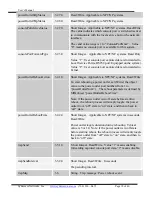
Model
Ethernet
(10 based-T)
Port
Local Master
RS232 Port
User
RS232 Port
Buffers for User RS-232 Port
NC-16
1
1
16
32 K Bytes for active serial port
NC-08
1
1
8
32 K Bytes for active serial port
Figure 1 - List of System Interface Ports for NC Systems
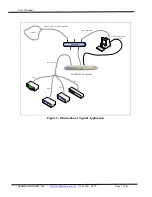
The NC systems provide secure and versatile console port t management for communication
equipment such as routers, switches, and network devices. They are also the ideal assistant
devices for engineering development and test applications. Key features include:
•
Data traffic from all user serial ports is serviced by a single TCP/IP session or the local
Master serial port. At any given time, only one user serial port is active for exchanging
data with the TCP/IP session or a local Master serial port. Data traffic on inactive ports is
not buffered and data is lost.
•
Local console port access
: offers data rates from 2400 to 115200 bits/seconds and
optional hardware handshaking (CTS/RTS).
•
Local Master Port access:
offers data rates from 2400 to 115200 bits/second and
optional hardware handshaking (CTS/RTS). There are two operation modes for the port:
Console Transparent Mode and System Control Mode.
•
Three user privilege login levels:
The Administration level manages system
configuration and unconditional access to all power outlets and all serial ports. The User
level allows each user to reserve and manage his/her own ports, as well as to change most
of system configuration settings. Anonymous users are able to view all settings and
operate unreserved power outlets and serial console ports.
•
User name and password for each port:
Each port is user name and password protected.
•
Line commands or menu configuration controls:
Menu table operation offers
user-friendly operation methods that are used for changing system configurations,
viewing run time statuses, and issuing controls. Line commands provide quick and easy
operations.
•
Network Access Filtering and Blocking:
When the system connection is established
through a TCP/IP network, you can setup up the system to block or permit an IP address or
a group of IP addresses. This is done by filling an ACL (Access Control List) data entry
table. The default setting is ACL off, which means all IP accesses are welcome.