Page 16
Scenario B: Configuring Your Network Interface
Configure your SonicWALL SSL-VPN 4000 to connect with your SonicWALL UTM
appliance under network configurations given in Scenario B.
On your SonicWALL SSL-VPN 4000:
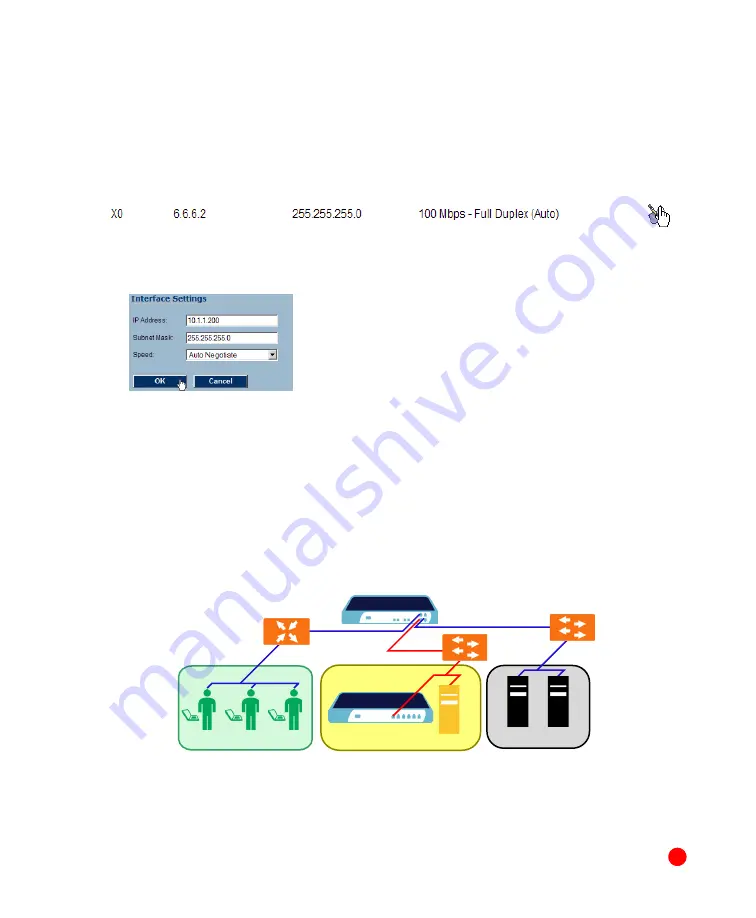
1. Select the
Network > Interfaces
page.
2. Click the
Configure
button for the
X0
port.
3. If configuring with
Scenario B
, enter an unused IP address in your DMZ subnet in
the
IP Address
field.
4. Enter your subnet mask in the
Subnet Mask
field.
5. Click the
OK
button to apply changes.
Scenario B: Connecting the SonicWALL SSL-VPN 4000
To connect the SonicWALL SSL-VPN 4000 using Scenario B, perform the following
steps:
1. Connect one end of an Ethernet cable to an unused port on your DMZ, either directly
to the
OPT
or
X2
on your existing SonicWALL UTM appliance or to a hub or switch
on your DMZ.
Scenario B:
SSL-VPN on an Existing DMZ
2. Connect the other end of the Ethernet cable to the
X0
port on the front of your
SonicWALL SSL-VPN 4000. The
X0
Port LED lights up green indicating an active
connection.
SonicWALL UTM PRO 5060
Existing DMZ
X1
X0
X2
SonicWALL SSL-VPN 4000
X0
Router
Switch/
Hub
Remote Users
Network Nodes
Network Node
Internet Zone
LAN
Switch/
Hub
6
















































