SANGFOR IAM v2.1 User Manual
118
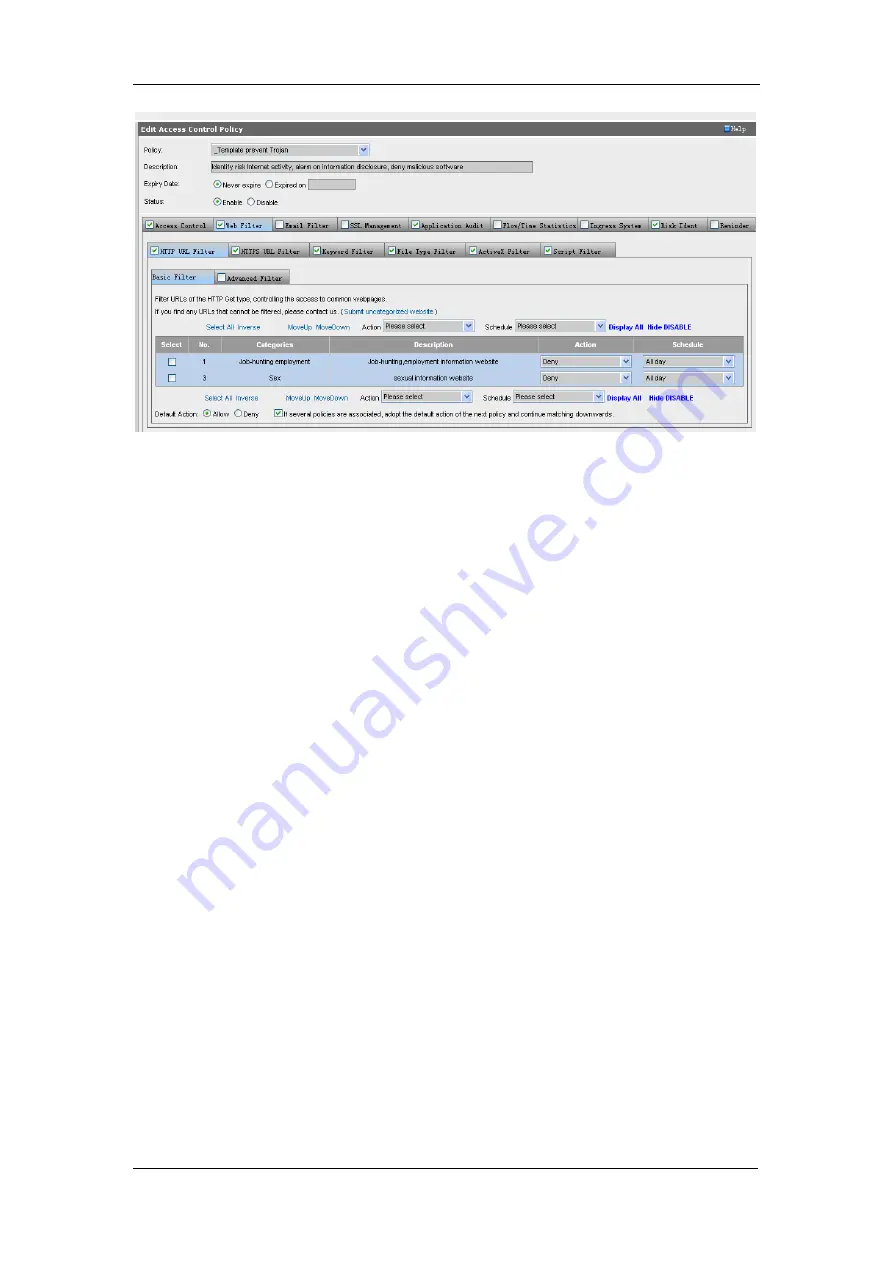
[Action]: Select [Disable], [Deny] or [Allow] define the status of the selected URL(s).
[Schedule]: Select [All day], [On duty], [Off duty] or [Internet access total time] to define the
valid time of the selected URL(s). As to detailed configuration of [Schedule], please refer to
Section 4.5 Schedule.
<Select All>, <Inverse>: Click this button to quickly select the needed URLs.
<Move Up>, <Move Down>: Click the button to move up or move down the corresponding
selected URL(s).
<Display All>: Click this button to display all the URLs, including the valid URLs and the invalid
URLs.
<Hide DISABLE>: Click this button to list all the valid URLs and hide all the invalid URLs.
[Default Action]: Select [Allow] or [Deny] to configure the default action of the current access
control policy to the HTTP URL filter rules that are not in the above rule list. This item functions
in association with the valid URL(s) configured above.
[If several policies are associated, adopt the default action of the next policy and continue
matching downwards]: If multiple access control policies are associated with a user or user group,
uncheck this item and the [Default Action] of the current policy will be adopted after the data
packets complete matching its rules; or check this item and the data packets will continue to match
the URL filtering rules of the access control policies followed.






























