ProSecure Web/Email Security Threat Management (STM) Appliance Reference Manual
Monitoring System Access and Performance
6-27
v1.0, September 2009
4.
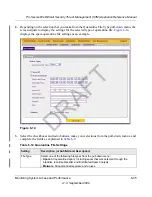
Click one of the following action buttons:
•
Search
.
Query the log according to the search criteria that you specified and view the log
through the Web Management Interface, that is, on screen.
•
Download
.
Query the log according to the search criteria that you specified and download
the log to a computer.
Example: Using Logs to Identify Infected Clients
You can use the STM logs to help identify potentially infected clients on the network. For
example, clients that are generating abnormally high volumes of HTTP traffic might be infected
with spyware or a virus.
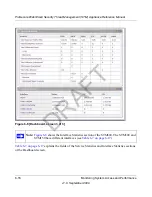
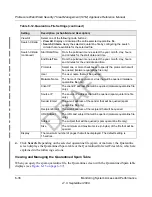
Search Criteria
(continued)
URL/Subject
The URL and subject that will be queried.
This field is available for the following logs
:
Traffic, Virus, and Spyware.
URL
The URL that will be queried.
This field is available only for the Content filters log
.
Category
The Web or application category that will be queried.
This field is available for the following logs
:
Content filters and Application.
Size
The minimum and maximum size (in bytes) of the file that will be
queried.
This field is available only for the Traffic log
.
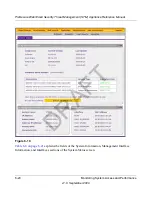
Type
Select one or more checkboxes to specify the system event type
that will be queried: error (all system errors), info (all informational
messages), conf. (all configuration changes), and update (all
system software updates).
This field is available only for the System log
.
Event
The description of the event incident that will be queried.
This field is available only for the System log
.
Section
The application group (Instant Messaging. Media Applications,
Peer to Peer, or Tools) that will be queried.
This field is available only for the Application log
.
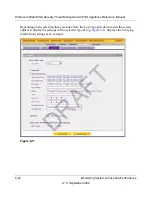
Display
The maximum number of pages that will be displayed. The default setting is 15
entries.
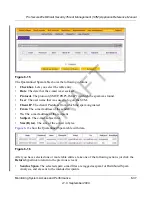
Download Log
(zipped) File
Format
Select a radio button to specify the format to download the zipped log file:
•
CSV
. Download the log file as a comma separated values (CSV) file.
•
HTML
. Download the log file as an HTML file.
Table 6-9. Logs Query Settings
<<Reorder Search Criteria rows in table? TBD.>>
Setting
Description (or Subfield and Description)
DRAFT