A
PPENDICES
S
ECTION
A
PPENDIX
A
M86 S
ECURITY
U
SER
G
UIDE
147
Windows XP SP2 Pop-up Blocker
This sub-section provides information on setting up pop-up
blocking and disabling pop-up blocking in Windows XP SP2.
Set up Pop-up Blocking
There are two ways to enable the pop-up blocking feature in
the IE browser.
Use the Internet Options dialog box
1. From the IE browser, go to the toolbar and select
Tools >
Internet Options
to open the Internet Options dialog
box.
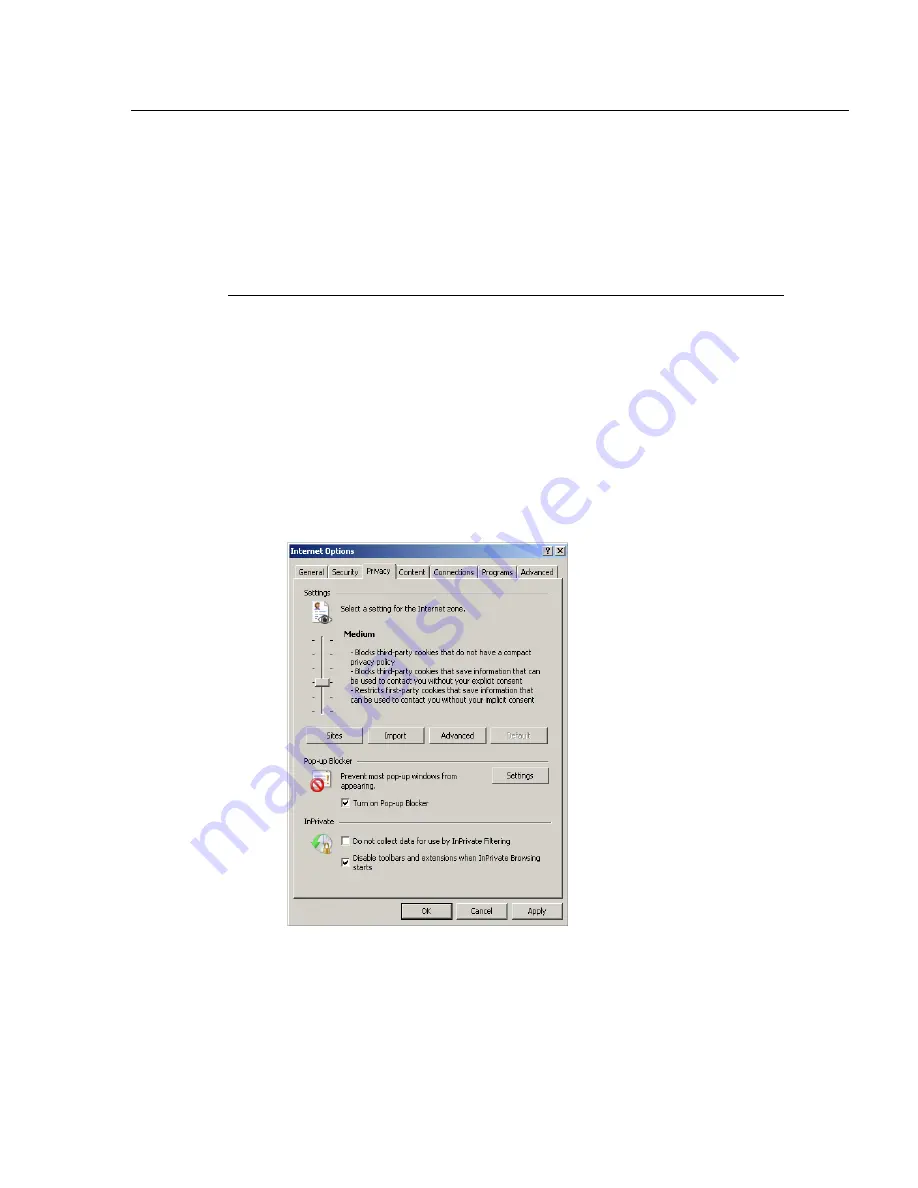
2. Click the Privacy tab:
Fig. A-7 Enable pop-up blocking
3. In the Pop-up Blocker frame, check “Turn on Pop-up
Blocker”.






























