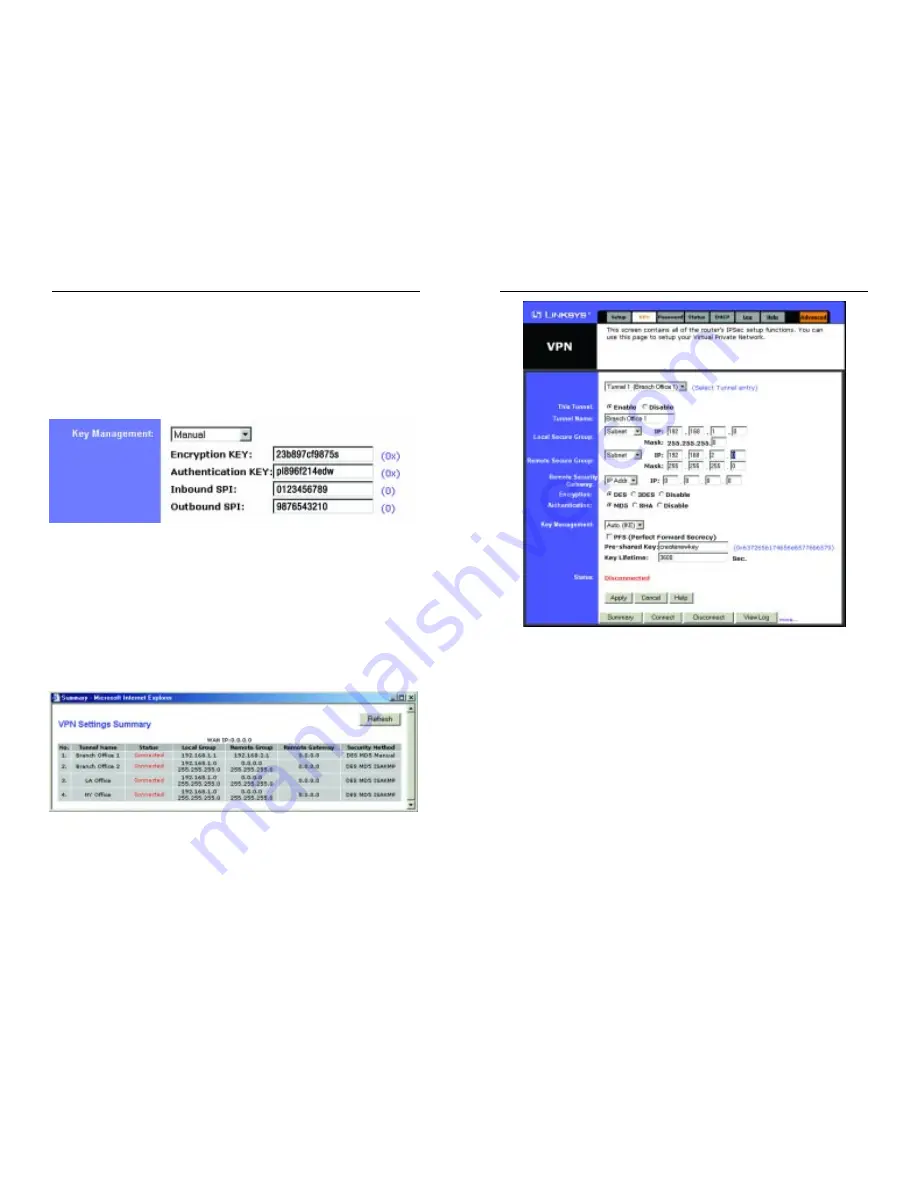
Under Status, the word Connected should appear if the connection is success-
ful. The other fields reflect the information that you entered on the VPN screen
to make the connection.
If Disconnected appears under Status, as shown in Figure 6-20, some problem
exists that prevents the creation of the tunnel. Make sure that all of your wiring
is securely connected. Double-check all the values you entered on the VPN
screen to make sure they are correct. If the other end of the tunnel is some dis-
tance from you (e.g., in another city, etc.), call to make sure that the settings on
that end of the tunnel are correct as well.
If, for any reason, you experience a temporary disconnection, the connection will
be re-established as long as the settings on both ends of the tunnel stay the same.
Figure 6-20
EtherFast
®
Cable/DSL VPN Router with 4-Port 10/100 Switch
The Inbound SPI and Outbound SPI fields are different, however. The
Inbound SPI value set here must match the Outbound SPI value at the other end
of the tunnel. The Outbound SPI here must match the Inbound SPI value at the
other end of the tunnel. In the example (see Figure 6-18), the Inbound SPI and
Outbound SPI values shown would be opposite on the other end of the tunnel.
Only numbers can be used in these fields. After you click the Apply button,
hexadecimal characters (series of letters and numbers) are displayed in the
Inbound SPI and Outbound SPI fields.
Once you are satisfied with all your settings, click the Apply button. If you
make any mistakes, clicking the Cancel button will exit the screen without sav-
ing any changes, provided that you have not already clicked the Apply button.
After the VPN device is set up at the other end of the tunnel, you may click the
Connect button to use the tunnel. This assumes that both ends of the tunnel
have a physical connection to each other (e.g., over the Internet, physical
wiring, etc.). After clicking the Connect button, click the Summary button. If
the connection is made, the screen shown in Figure 6-19 will appear:
Figure 6-18
Figure 6-19
Instant Broadband
®
Series
33
32
















































