9-35
Configuring and Monitoring Port Security
Reading Intrusion Alerts and Resetting Alert Flags
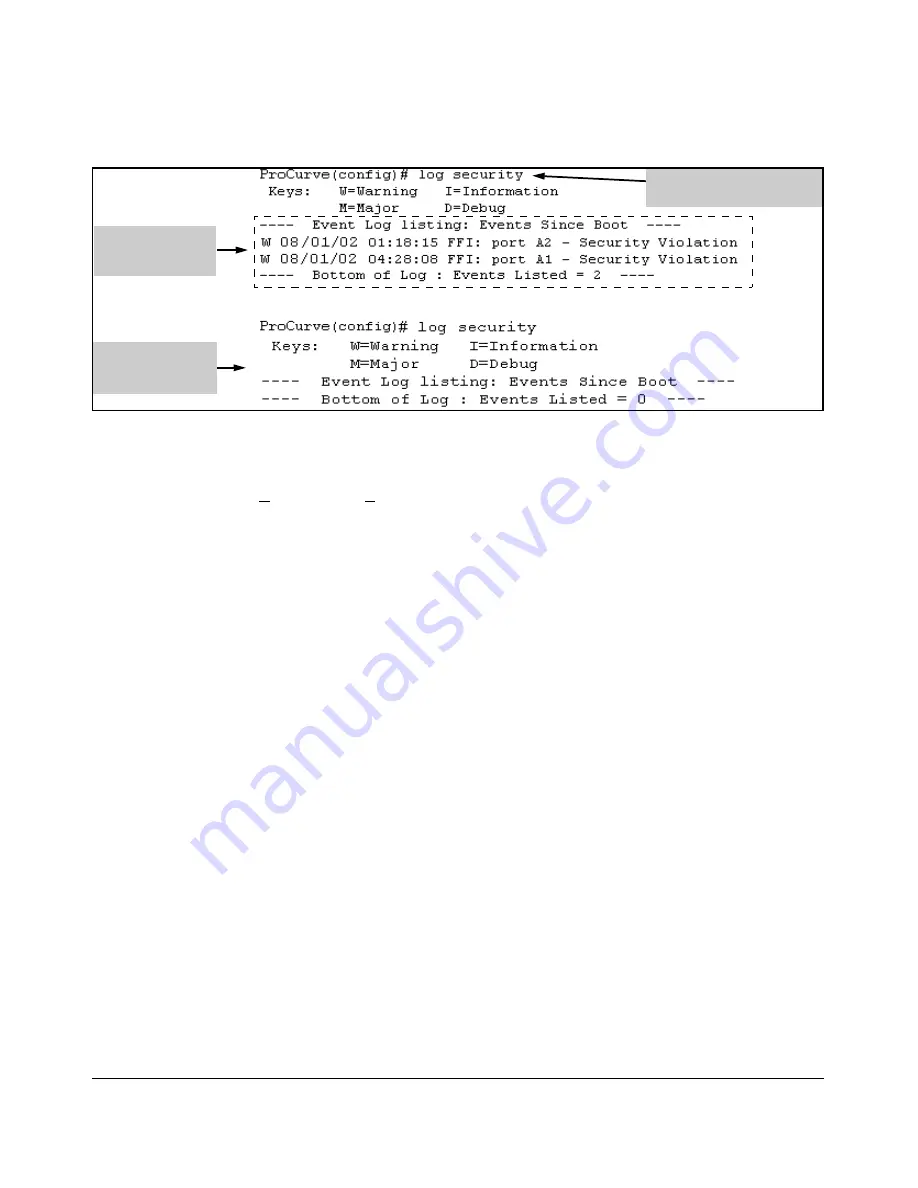
Figure 9-19. Example of Log Listing With and Without Detected Security Violations
From the Menu Interface:
In the Main Menu, click on
4. Event Log
and use
Next page
and
Prev page
to review the Event Log contents.
For More Event Log Information.
See “Using the Event Log To Identify
Problem Sources” in the “Troubleshooting” chapter of the
Management and
Configuration Guide
for your switch.
Web: Checking for Intrusions, Listing Intrusion Alerts,
and Resetting Alert Flags
1.
Check the Alert Log by clicking on the
Status
tab and the
[
Overview]
button. If there is a “Security Violation” entry, do the following:
a.
Click on the
Security
tab.
b.
Click on
[Intrusion Log]
. “Ports with Intrusion Flag” indicates any ports
for which the alert flag has not been cleared.
c.
To clear the current alert flags, click on
[Reset Alert Flags]
.
To access the web-based Help provided for the switch, click on
[?]
in the web
browser screen.
Log Listing with
Security Violation
Detected
Log Listing with No
Security Violation
Detected
Log Command with “security”
for Search String
Summary of Contents for ProCurve 2510G Series
Page 1: ...Access Security Guide www procurve com ProCurve Series 2510G Switches Y 11 XX ...
Page 2: ......
Page 3: ...ProCurve Series 2510G Switches Access Security Guide June 2008 ...
Page 12: ...x ...
Page 26: ...1 10 Getting Started Need Only a Quick Start ...
Page 105: ...4 31 TACACS Authentication Configuring TACACS on the Switch ...
Page 106: ...4 32 TACACS Authentication Configuring TACACS on the Switch ...
Page 176: ...6 30 Configuring Secure Shell SSH Messages Related to SSH Operation ...
Page 198: ...7 22 Configuring Secure Socket Layer SSL Common Errors in SSL Setup ...
Page 296: ...9 40 Configuring and Monitoring Port Security Configuring Protected Ports ...
Page 310: ...10 14 Using Authorized IP Managers Operating Notes ...
Page 318: ...8 Index ...
Page 319: ......






























