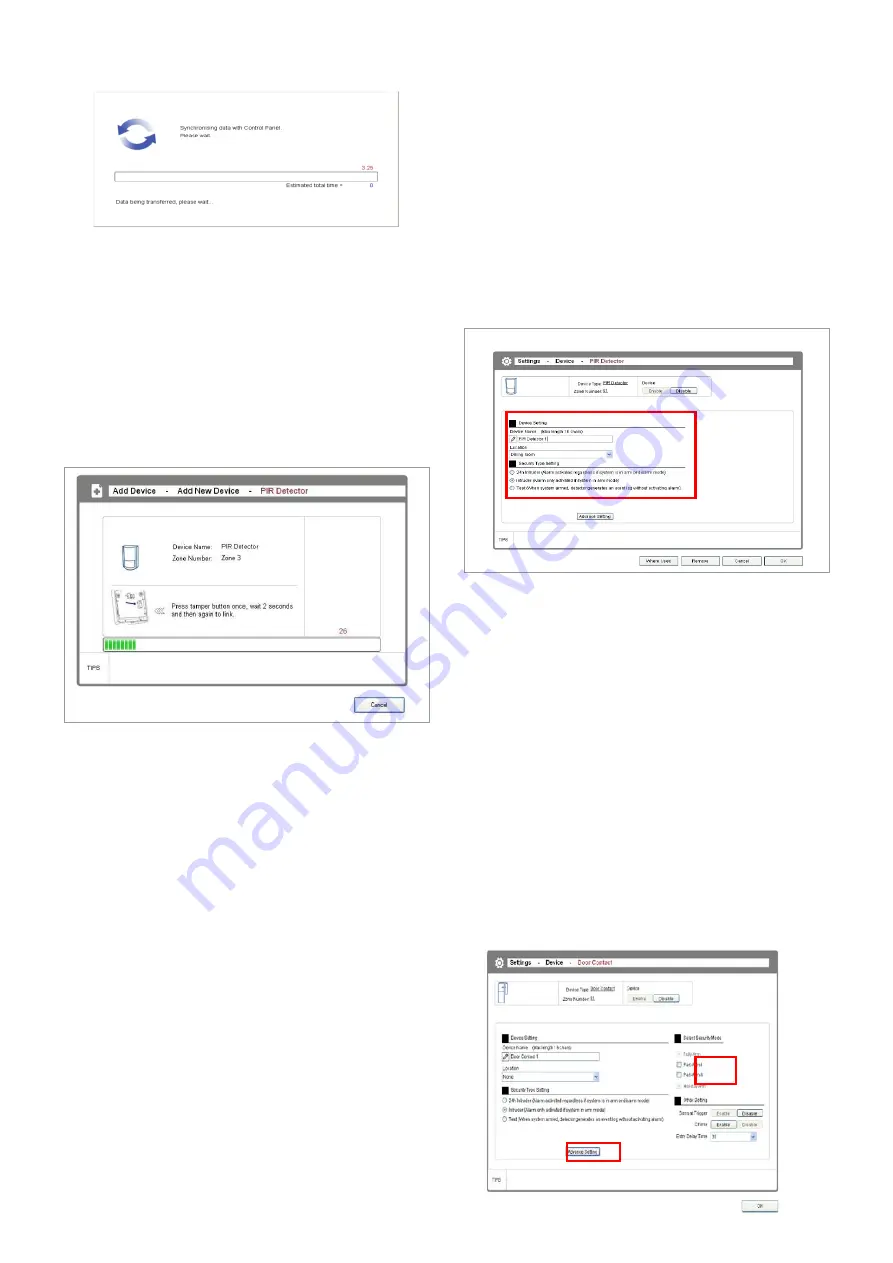
10
2. The software will issue a request to the Control
Panel to go into code learning mode.
3. Press the learn/tamper button on the selected PIR
detector within 30 seconds to transmit a code to be
picked up by the Control Panel.
Note: See the screen prompt (also the figure below)
to find out the location of the learn/tamper button
on the device. After you press the learn/tamper
button, the Control Panel will also beep to indicate
the reception of the learning code.
4. Once the system has learnt the device’s code, the
device setting window will appear up for you to
configure the device’s name, location, and security
type:
Name:
Specify a name for easy identification.
Location:
Specify where the device is installed.
Security Type:
Specify the level of alarm when the
device is triggered.
5. After adding/replacing a security device (PIR or
door/window contact detector) to the system, refit the
detector in position to its battery cover before exiting
the add device screen. This is will prevent the tamper
alarm from initiating if the tamper button is press and
release during final installation of a detector.
IMPORTANT: Specify the Location of device
carefully as it affects many aspects in the system:
1) If one or more IP cameras are installed in your
system, then when a PIR or other type of detector
is triggered, the camera assigned to the SAME
location will start recording. Therefore you should
plan beforehand and assign the location group
carefully.
2) When the device is triggered, the Web software
and the smartphone app will also inform the user
of the location. So the correct setting of location is
critical for the information.
3) After a security detector such as a wireless PIR
or door contact detector has been added, the
device number is the “Zone Number” (1-36)
displayed at the top of the window. The zone
number for each security device is stored in the
Control Panel
Part-ArmI/II setup of a security device
All PIR movement and door/window contact security
detectors can be also setup to operate with Part-Arm I
or Part-Arm II security modes.
If a group of detectors have been set so that they can
activate in Part-Arm I, this means that when the Control
Panel is armed in Part-Arm I mode, then only those
detectors setup will become active. An example would
be part-arming the ground floor of your home while you
are gone to sleep so you can move around upstairs at
night without initiating an alarm
Part arm setup of a device can be done during the
adding process or after the device has been added
in “Settings – Devices”.




















