Public Key Infrastructure
225/263
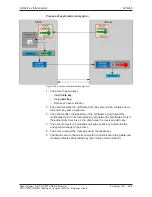
Process of asymmetric encryption
Figure 145: Process of asymmetric encryption
1. The server has two keys
–
the
private key
–
the
public key
–
Both keys have a relation.
2. The client receives the certificate from the server which contains even
the public key and a signature.
3. The client verifies the signature of the certificate using trustworthy
certificates stored in its local directory of trustworthy certificates. Only if
the authenticity check is ok, the client uses the received public key.
4. The client encrypts the message using the public key and sends the
encrypted message to the server.
5. The server decrpyt the message using his private key.
6. Client and server continue its encrypted communication using
one
new
created protected transmitted key (symmetric communication).
Edge Gateway | NIOT-E-TIB100-GB-RE (Remote)
DOC170501UM04EN | Revision 4 | English | 2018-08 | Released | Public
© Hilscher 2017 – 2018