3-33
After the configuration, when you log in to the device through the console port at the next time, you are
prompted to enter a login password. A prompt such as <H3C> appears after you input the password
and press
Enter
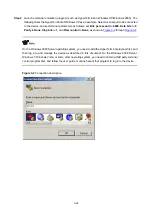
, as shown in
.
Figure 3-7
Configuration page
Configuring Scheme Authentication for Console Login
Configuration prerequisites
You have logged in to the device.
By default, you can log in to the device through the console port without authentication and have user
privilege level 3 after login. For how to log in to the device with default configuration, see
.
Configuration procedure
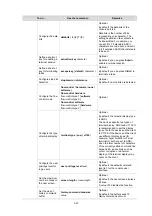
Follow these steps to configure scheme authentication for console login:
To do…
Use the command…
Remarks
Enters system view
system-view
—
Enter console user interface
view
user-interface console
first
-
number
[
last-number
]
—
Specify the scheme
authentication mode
authentication-mode
scheme
Required
Whether local, RADIUS, or
HWTACACS authentication is
adopted depends on the configured
AAA scheme.
By default, users that log in through
the console port are not
authenticated.
Summary of Contents for SR6600 SPE-FWM
Page 112: ...6 101...