Machine Administrator Settings
135
8
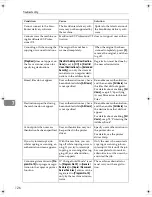
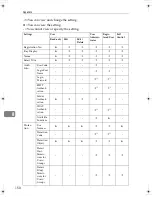
Printer Features
The following settings can be specified.
❖
List / Test Print
All the settings can be specified.
❖
Maintenance
• Menu Protect
• List / Test Print Lock
❖
System
The following settings can be specified.
• Print Error Report
• Auto Continue
• Memory Overflow
• Job Separation
• Initial Print Job List
• Memory Usage
• Memory Usage
• Copies
• Blank Page Print
• Edge Smoothing
• Toner Saving
• Printer Language
• Sub Paper Size
• Page Size
• Letterhead Setting
• Bypass Tray Setting Priority
• Edge to Edge Print
• Default Printer Language
• Tray Switching
❖
Host Interface
All the settings can be specified.
❖
PCL Menu
*1
All the settings can be specified.
D0086951_RussianC45-EN.book Page 135 Wednesday, May 31, 2006 11:45 AM
Summary of Contents for DSm725e
Page 8: ...2...