40
Processor
If the system load is high, a fast processor on the Microsoft Exchange
Server speeds up the e-mail message processing. As Microsoft
Exchange Server handles a large amount of data, a fast processor alone
is not enough to guarantee a fast operation of F-Secure Anti-Virus for
Microsoft Exchange.
Memory
Memory consumption is directly proportional to the size of processed
mails - scanning a single mail may use memory in amounts up to three
times the size of the mail concerned. If the average size of mail messages
is big, or Microsoft Exchange Server has to process large messages
regularly, increasing the amount of physical memory increases the overall
performance.
If large messages are processed only now and then, it might be enough
to increase the size of the virtual memory. In this case, large messages
will slow the system down.
Hard Drive
Hard drive size is an important reliability factor. Hard drive performance is
crucial for Microsoft Exchange Server to perform well. For best
performance, a RAID system is recommended; for servers with only
moderate load, SCSI hard disks are adequate. If your server has an IDE
hard disk, DMA access support is recommended.
Operating
System
It is highly recommended to have the latest service packs for the
operating system being used. These fixes make the platform more stable
and thus increase the reliability of the system.
3.5
Centrally Administered or Stand-alone
Installation?
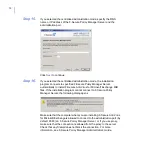
F-Secure Anti-Virus for Microsoft Exchange can be managed either with
F-Secure Anti-Virus for Microsoft Exchange Web Console or F-Secure
Policy Manager Console. You can select the management method when
you install the product.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......