APPENDIX A
103
Deploying the Product on a Cluster
A.7
Uninstallation
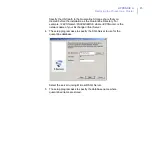
Follow these instructions to uninstall the product in the cluster
environment.
1.
Uninstall the product from the active node with Add/Remove
Programs in Windows 2003 or Programs and Features in Windows
2008 and 2008 R2. The uninstallation removes the cluster resource
automatically.
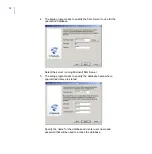
2.
After the uninstallation in the active node is finished, uninstall the
product from passive nodes.
3.
After the product has been uninstalled from every node, reboot
computers one at the time.
A.8
Troubleshooting
If the product fails to quarantine a file or reports that the
quarantine storage is not accessible, make sure that directory
sharing and security permissions are set as follows:
change
,
write
and
read
operations are allowed for
SYSTEM
and
Exchange
Domain Servers
, and
full control
is allowed for
Administrator
.
To change the location of the quarantine storage from F-Secure
Policy Manager Console, use the
Final
flag to override the setting
set during product installation on the host.
Summary of Contents for ANTI-VIRUS FOR MICROSOFT EXCHANGE 9.00
Page 1: ...F Secure Anti Virus for Microsoft Exchange Deployment Guide...
Page 6: ...4 ABOUT THIS GUIDE How This Guide Is Organized 5 Conventions Used in F Secure Guides 6...
Page 19: ...17 2 DEPLOYMENT Installation Modes 18 Network Requirements 19 Deployment Scenarios 20...
Page 64: ...62 4 CONFIGURING F SECURE SPAM CONTROL Overview 63 Realtime Blackhole List Configuration 64...
Page 106: ...104 B APPENDIX Services and Processes List of Services and Processes 105...
Page 115: ......