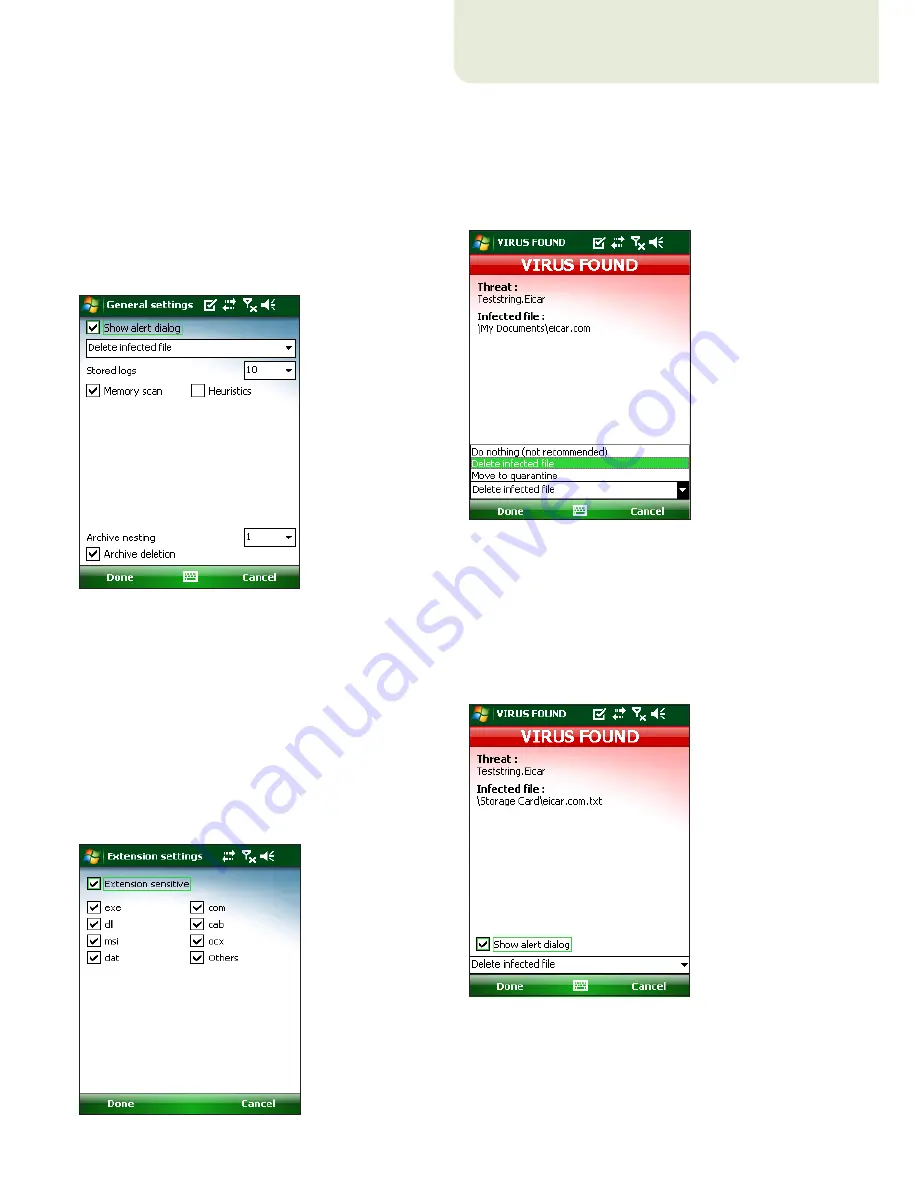
10
If the
Heuristics
option is selected, ESET Mobile
Antivirus uses heuristic scanning techniques. Heuristics
is an algorithm‑based detection method that analyzes
the code and searches for typical virus behavior. Its main
advantage is the ability to identify malicious software
not yet known by the current virus signature database.
Archive nesting
allows you to specify the depth of
nested archives to be scanned.
Select
Archive deletion
to automatically
delete archive files containing infected objects.
Figure 3-6: General settings
3.4 Scan objects setup
To specify the file types to be scanned on your mobile
device, tap
Menu > Settings > Extensions
.
The
Extension settings
window will display (Figure
3‑7), showing the most common file types exposed to
infiltration. Select the file types you wish to be scanned.
To exclude an extension from scanning, deselect its
check box.
To scan all files, deselect the
Extension sensitive
check box.
Figure 3-7: Advanced scan parameter setup
4. Virus found
If a virus is found, ESET Mobile Antivirus will prompt
you to take an action. We recommend you select
Delete infected file
. If you select
Do nothing (not
recommended)
, no action will be performed and the
infected file will remain on your mobile device. If you
select
Move to quarantine
, the file will be moved to
quarantine and deleted.
Figure 4-1: Action if a virus is found
When a virus is detected, ESET Mobile Antivirus displays
the
Show alert dialog
check box. Deselect this option
to prevent alert windows from displaying in the future.
All future actions will be performed automatically.
NOTE:
If an infiltration is detected in an archive, the
Delete archive
option is available in the alert window.
Select this option along with the
Delete infected file
option to delete all infected archive files.
Figure 4-2: Virus found


































