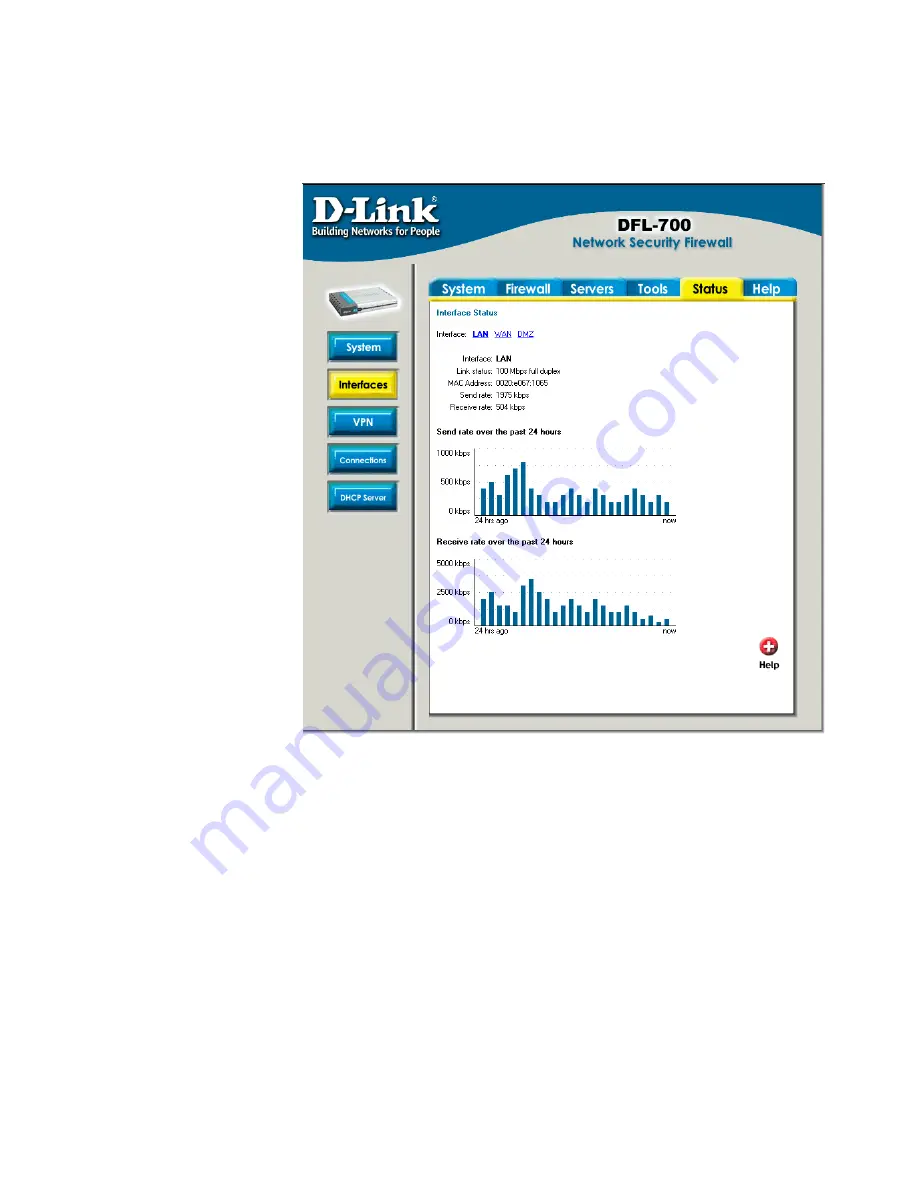
Interfaces
Click on
Status
in the menu bar, and then click
Interfaces
below it. A window will appear
providing information about the interfaces in the DFL-700. By default information about the
LAN
interface will be show, to see another one click on that interface (
WAN
or
DMZ
).
Interface
– Name of
the interface shown,
LAN, WAN or DMZ.
Link status
–
Displays what link the
current interface has,
the speed can be 10 or
100 Mbps and the
duplex can be Half or
Full.
MAC Address
–
MAC address of the
interface.
Send rate
– Current
amount of traffic sent
trough the interface.
Receive rate
–
Current amount of traffic
received trough the
interface.
There are also two
graphs displaying the
send and receive rate
trough the interfaces
during the last 24 hours.
Summary of Contents for DFL-700 - Security Appliance
Page 1: ...D Link DFL 700 Network Security Firewall Manual Building Networks for People Ver 1 02 20050419...
Page 106: ...106 5 Select Connect to the network at my workplace and click Next...
Page 107: ...6 Select Virtual Private Network connection and click Next...
Page 108: ...108 7 Name the connection MainOffice and click Next...
Page 109: ...8 Select Do not dial the initial connection and click Next...
Page 110: ...110 9 Type the IP address to the server 194 0 2 20 and click Next 10 Click Finish...
Page 136: ...136 Consult the dealer or an experienced radio TV technician for help VCCI Warning...
Page 139: ......
Page 140: ...140...
Page 141: ......






























