Phantom II
© CalAmp
28
5.1 Network Topologies
Example 5.2.1 (continued)
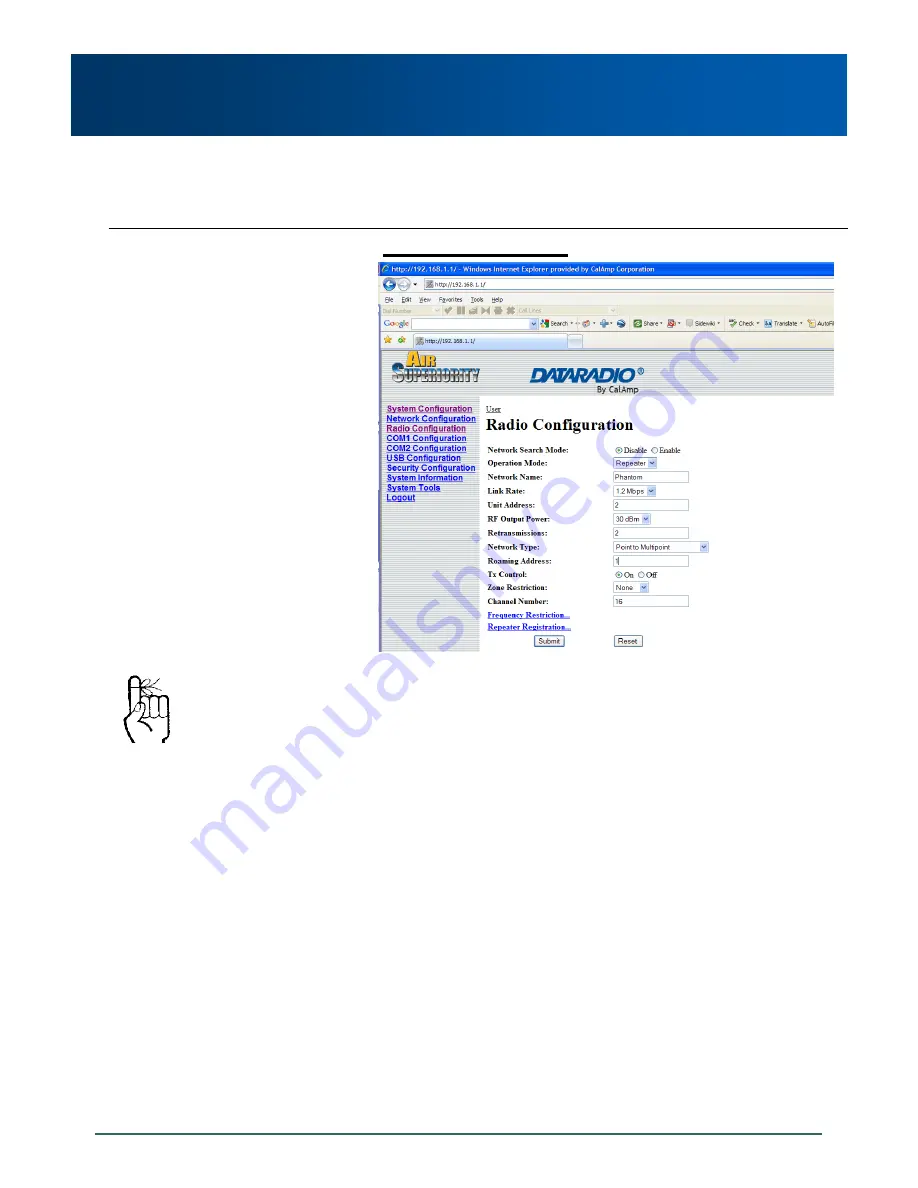
Image 5-4: PMP Example 5.2.1: Repeater
When bench testing PMP with a
REPEATER in the network,
configure the REMOTE to
synchronize to the REPEATER
via the
REMOTE’s ROAMING
ADDRESS field. If this is not
done, with the REMOTE in close
proximity to the MASTER and its
ROAMING set as 1 (default), the
REMOTE will simply synchronize
with (and pass data directly to)
the MASTER, bypassing the
REPEATER altogether.
The ROAMING address for the REPEATER is set to 1:
the UNIT ADDRESS of the MASTER. This means that
this REPEATER will synchronize to, and communicate
directly with, the MASTER.
There is no DESTINATION UNIT field for remote units
in a PMP network: the destination is predefined as
‘1’ (the MASTER ‘point’).
On the following page are the configurations for the REMOTES.
Remote 20’s ROAMING ADDRESS is set to 2, the
UNIT ADDRESS of the REPEATER. This Remote will
synchronize to the Repeater and communicate via the
Repeater to the Master.
Remote 30’s ROAMING ADDRESS is set to 1 (the
UNIT ADDRESS of the MASTER): it will synchronize
to, and communicate directly with, the MASTER.
Summary of Contents for Phantom II
Page 160: ...Phantom II CalAmp 160 Appendix E Customer Interface Schematic 1 of 3 ...
Page 161: ...Phantom II CalAmp 161 Appendix E Customer Interface Schematic 2 of 3 ...
Page 162: ...Phantom II CalAmp 162 Appendix E Customer Interface Schematic 3 of 3 ...
Page 164: ...299 Johnson Ave Suite 110 Waseca MN 56093 Phone 800 992 7774 Fax 507 833 6748 www calamp com ...
















































