ClearPass Guest 3.9 | Deployment Guide
Guest Management |
253
column are also shown in the list view. Values displayed in
italics
are default values defined for the field
being displayed.
Click a view field in the list view to select it.
Use the
Edit
link to make changes to an existing column using the view field editor. Any changes made
to the field using this editor will apply only to this field on this view.
Use the
Edit Base Field
link to make changes to an existing field definition. Any changes made to the
field using this editor will apply to all views that are using this field (except where the view field has already
been modified to be different from the underlying field definition).
The
Insert Before
and
Insert After
links can be used to add a new column to the view. Clicking
one of these links will open a blank view field editor and automatically set the rank number of the new
column.
Use the
Enable Field
and
Disable Field
links to quickly turn the display of a column on or off.
Click the
Add Field
tab to add a new column to the view.
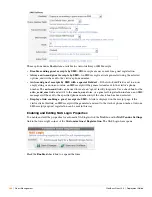
View Field Editor
The view field editor is used to control the data-display aspects of a column within the view.
.
Each column in a view displays the value of a single field.
To use the default view display properties for a field, you only need to select the field to display in the
column and then click the
Save Changes
button.
To customize the view display properties, click the
Advanced view options…
check box.
The column type must be one of the following:
Text
– The column displays a value as text.
Sortable text
– The column displays a value as text, and may be sorted by clicking on the column
heading.
Sortable text, case-insensitive
– The same as “Sortable text”, but the column sorting will treat
uppercase and lowercase letters the same.
Sortable numeric
– The column displays a numeric value, and may be sorted by clicking on the column
heading.
Summary of Contents for ClearPass Guest 3.9
Page 1: ...ClearPass Guest 3 9 Deployment Guide ...
Page 32: ...32 Management Overview ClearPass Guest 3 9 Deployment Guide ...
Page 178: ...178 RADIUS Services ClearPass Guest 3 9 Deployment Guide ...
Page 316: ...316 Guest Management ClearPass Guest 3 9 Deployment Guide ...
Page 410: ...410 Administrator Tasks ClearPass Guest 3 9 Deployment Guide ...
Page 414: ...414 Administrator Tasks ClearPass Guest 3 9 Deployment Guide ...
Page 423: ...ClearPass Guest 3 9 Deployment Guide Hotspot Manager 423 ...
Page 440: ...440 High Availability Services ClearPass Guest 3 9 Deployment Guide ...
Page 518: ...518 Index ClearPass Guest 3 9 Deployment Guide ...