Chapter 28 DHCP Snooping
XGS4600 Series User’s Guide
301
C
HAPTER
28
DHCP Snooping
28.1 DHCP Snooping Overview
With DHCP snooping, the Switch can build the binding table dynamically by snooping DHCP packets
(dynamic bindings) and filter unauthorized DHCP packets in your network.
The Switch uses a binding table to distinguish between authorized and unauthorized DHCP packets in
your network. A binding contains these key attributes:
• MAC address
• VLAN ID
• IP address
• Port number
When the Switch receives a DHCP packet, it looks up the appropriate MAC address, VLAN ID, IP
address, and port number in the binding table. If there is a binding, the Switch forwards the packet. If
there is not a binding, the Switch discards the packet.
28.1.1 What You Can Do
• Use the
DHCP Snooping
screen (
) to look at various statistics about the DHCP
snooping database.
• Use this
DHCP Snooping Configure
screen (
) to enable DHCP snooping on
the Switch (not on specific VLAN), specify the VLAN where the default DHCP server is located, and
configure the DHCP snooping database.
• Use the
DHCP Snooping Port Configure
screen (
) to specify whether ports
are trusted or untrusted ports for DHCP snooping.
• Use the
DHCP Snooping VLAN Configure
) to enable DHCP
snooping on each VLAN and to specify whether or not the Switch adds DHCP relay agent option 82
information to DHCP requests that the Switch relays to a DHCP server for each VLAN.
• Use the
DHCP Snooping VLAN Port Configure
screen (
) to apply a different
DHCP option 82 profile to certain ports in a VLAN.
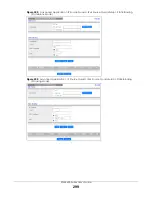
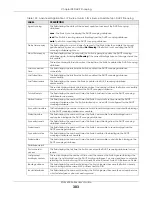
28.2
DHCP Snooping
Use this screen to look at various statistics about the DHCP snooping database.
To open this screen, click
Advanced Application
>
IP Source Guard
>
IPv4 Source Guard Setup
>
DHCP
Snooping
.
Содержание XGS4600 Series
Страница 24: ...24 PART I User s Guide ...
Страница 44: ...44 PART II Technical Reference ...
Страница 180: ...Chapter 13 Spanning Tree Protocol XGS4600 Series User s Guide 180 Figure 145 MSTP and Legacy RSTP Network Example ...
Страница 189: ...Chapter 16 Mirroring XGS4600 Series User s Guide 189 Figure 150 Advanced Application Mirroring Standalone Mode ...
Страница 244: ...Chapter 22 Policy Rule XGS4600 Series User s Guide 244 Figure 189 Policy Example EXAMPLE ...
Страница 277: ...Chapter 25 Multicast XGS4600 Series User s Guide 277 Figure 215 Advanced Application Multicast MVR Standalone Mode ...
Страница 559: ...Chapter 59 Access Control XGS4600 Series User s Guide 559 Figure 460 Example Lock Denoting a Secure Connection EXAMPLE ...
Страница 586: ...Chapter 69 Configure Clone XGS4600 Series User s Guide 586 Figure 479 Management Configure Clone Standalone Mode ...
Страница 587: ...Chapter 69 Configure Clone XGS4600 Series User s Guide 587 Figure 480 Management Configure Clone Stacking Mode ...
Страница 594: ...Chapter 71 Port Status XGS4600 Series User s Guide 594 Figure 485 Management Port Status Port Details Standalone Mode ...
Страница 604: ...604 PART III Troubleshooting and Appendices ...