P-660H/HW-T Series User’ Guide
Chapter 38 Troubleshooting
348
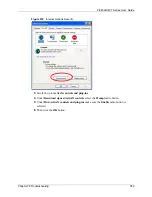
Figure 228
Internet Options
2
Click the
Custom Level...
button.
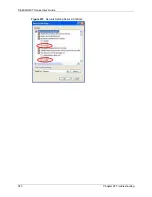
3
Scroll down to
Scripting
.
4
Under
Active scripting
make sure that
Enable
is selected (the default).
5
Under
Scripting of Java applets
make sure that
Enable
is selected (the default).
6
Click
OK
to close the window.
Содержание P-660H Series
Страница 2: ......
Страница 10: ...P 660H HW T Series User Guide 9 Customer Support ...
Страница 32: ...P 660H HW T Series User Guide 31 List of Figures ...
Страница 38: ...P 660H HW T Series User Guide 37 List of Tables ...
Страница 42: ...P 660H HW T Series User Guide 41 Introduction to DSL ...
Страница 62: ...P 660H HW T Series User Guide 61 Chapter 3 Wizard Setup for Internet Access ...
Страница 90: ...P 660H HW T Series User Guide 89 Chapter 5 Wireless LAN ...
Страница 132: ...P 660H HW T Series User Guide 131 Chapter 10 Firewalls ...
Страница 162: ...P 660H HW T Series User Guide 161 Chapter 13 Remote Management Configuration ...
Страница 176: ...P 660H HW T Series User Guide 175 Chapter 14 Universal Plug and Play UPnP ...
Страница 182: ...P 660H HW T Series User Guide 181 Chapter 15 Logs Screens ...
Страница 196: ...P 660H HW T Series User Guide 195 Chapter 16 Media Bandwidth Management Advanced Setup ...
Страница 208: ...P 660H HW T Series User Guide 207 Chapter 17 Maintenance ...
Страница 218: ...P 660H HW T Series User Guide 217 Chapter 19 Menu 1 General Setup ...
Страница 222: ...P 660H HW T Series User Guide 221 Chapter 20 Menu 2 WAN Backup Setup ...
Страница 226: ...P 660H HW T Series User Guide 225 Chapter 21 Menu 3 LAN Setup ...
Страница 230: ...P 660H HW T Series User Guide 229 Chapter 22 Wireless LAN Setup ...
Страница 236: ...P 660H HW T Series User Guide 235 Chapter 23 Internet Access ...
Страница 250: ...P 660H HW T Series User Guide 249 Chapter 25 Static Route Setup ...
Страница 254: ...P 660H HW T Series User Guide 253 Chapter 26 Bridging Setup ...
Страница 270: ...P 660H HW T Series User Guide 269 Chapter 27 Network Address Translation NAT ...
Страница 286: ...P 660H HW T Series User Guide 285 Chapter 29 Filter Configuration ...
Страница 306: ...P 660H HW T Series User Guide 305 Chapter 32 System Information and Diagnosis ...
Страница 318: ...P 660H HW T Series User Guide 317 Chapter 33 Firmware and Configuration File Maintenance ...
Страница 324: ...P 660H HW T Series User Guide 323 Chapter 34 System Maintenance ...
Страница 328: ...P 660H HW T Series User Guide 327 Chapter 35 Remote Management ...
Страница 338: ...P 660H HW T Series User Guide 337 Chapter 36 IP Policy Routing ...
Страница 342: ...P 660H HW T Series User Guide 341 Chapter 37 Call Scheduling ...
Страница 354: ...P 660H HW T Series User Guide 353 Chapter 38 Troubleshooting Figure 233 Security Setting ActiveX Controls ...
Страница 358: ...P 660H HW T Series User Guide 357 Appendix A ...
Страница 360: ...P 660H HW T Series User Guide 359 Appendix B ...
Страница 384: ...P 660H HW T Series User Guide 383 Appendix D ...
Страница 388: ...P 660H HW T Series User Guide 387 Appendix F ...
Страница 394: ...P 660H HW T Series User Guide 393 Appendix G ...
Страница 398: ...P 660H HW T Series User Guide 397 Appendix H ...
Страница 401: ...P 660H HW T Series User Guide Appendix I 400 ...
Страница 402: ...P 660H HW T Series User Guide 401 Appendix I ...
Страница 456: ...P 660H HW T Series User Guide 455 Appendix M ...