Содержание Dimension GS-2024
Страница 2: ......
Страница 7: ...Safety Warnings GS 2024 User s Guide 7 This product is recyclable Dispose of it properly ...
Страница 8: ...Safety Warnings GS 2024 User s Guide 8 ...
Страница 26: ...List of Tables GS 2024 User s Guide 26 ...
Страница 28: ...28 ...
Страница 36: ...Chapter 2 Hardware Installation and Connection GS 2024 User s Guide 36 ...
Страница 44: ...44 ...
Страница 62: ...Chapter 6 System Status and Port Statistics GS 2024 User s Guide 62 ...
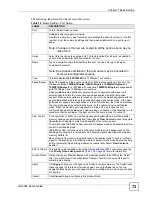
Страница 70: ...Chapter 7 Basic Setting GS 2024 User s Guide 70 Figure 27 Basic Setting IP Setup ...
Страница 74: ...Chapter 7 Basic Setting GS 2024 User s Guide 74 ...
Страница 76: ...76 ...
Страница 88: ...Chapter 8 VLAN GS 2024 User s Guide 88 ...
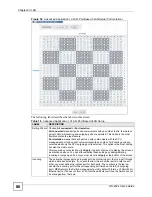
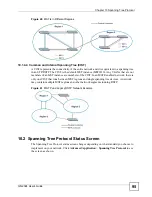
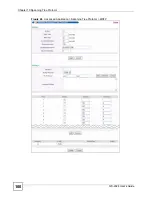
Страница 100: ...Chapter 10 Spanning Tree Protocol GS 2024 User s Guide 100 Figure 46 Advanced Application Spanning Tree Protocol MSTP ...
Страница 110: ...Chapter 13 Mirroring GS 2024 User s Guide 110 ...
Страница 120: ...Chapter 15 Port Authentication GS 2024 User s Guide 120 ...
Страница 138: ...Chapter 18 Multicast GS 2024 User s Guide 138 ...
Страница 152: ...Chapter 19 Authentication Accounting GS 2024 User s Guide 152 ...
Страница 157: ...157 PART IV IP Application Static Route 159 Differentiated Services 163 DHCP 167 ...
Страница 158: ...158 ...
Страница 162: ...Chapter 21 Static Route GS 2024 User s Guide 162 ...
Страница 166: ...Chapter 22 Differentiated Services GS 2024 User s Guide 166 ...
Страница 174: ...174 ...
Страница 198: ...Chapter 25 Access Control GS 2024 User s Guide 198 ...
Страница 200: ...Chapter 26 Diagnostic GS 2024 User s Guide 200 ...
Страница 204: ...Chapter 27 Syslog GS 2024 User s Guide 204 ...
Страница 217: ...217 PART VI Troubleshooting Product Specifications Troubleshooting 219 Product Specifications 223 ...
Страница 218: ...218 ...
Страница 222: ...Chapter 32 Troubleshooting GS 2024 User s Guide 222 ...
Страница 230: ...Chapter 33 Product Specifications GS 2024 User s Guide 230 ...
Страница 232: ...232 ...
Страница 240: ...Appendix A Pop up Windows JavaScripts and Java Permissions GS 2024 User s Guide 240 ...
Страница 252: ...Appendix C Legal Information GS 2024 User s Guide 252 ...
Страница 258: ...Appendix D Customer Support GS 2024 User s Guide 258 ...
Страница 266: ...Index GS 2024 User s Guide 266 ...