CHAPTER 1: Internet Protocol Reference
6
WatchGuard Firebox System
Internet Protocol Options
Internet Protocol options are variable-length additions to the standard IP
header. Unfortunately, enabling IP options can be risky; hackers can use
them to specify a route that helps them gain access to your network.
Because most applications make it very obscure or difficult to use IP
options, they are rarely used.
There are several kinds of IP options:
Security
Control routing of IP packets that carry sensitive data. Security
options are rarely supported.
Stream ID (SID)
The stream ID option is rarely supported.
Source Routing
Both the loose source route option and the strict source route
option enable the source of an Internet packet to provide routing
information. Source routing options can be very dangerous,
because a clever attacker might use them to masquerade as
another site. However, loose source routing and the traceroute
facility can also help debug some obscure routing problems.
Record Route
The record route option was originally intended for use in testing
the Internet. Unfortunately, record route can record only ten IP
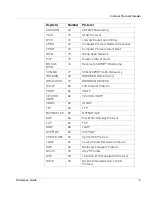
SCC-SP
96
Semaphore Communications Security
Protocol
ETHERIP
97
Ethernet-within-IP Encapsulation
ENCAP
98
Encapsulation Header
99
Any private encryption scheme
GMTP
100
GMTP
101-254 Unassigned
255
Reserved
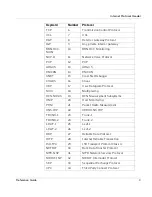
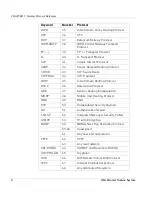
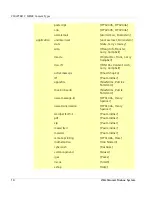
Keyword
Number
Protocol
Содержание Firebox X1000
Страница 1: ...WatchGuard Firebox System Reference Guide WatchGuard Firebox System...
Страница 12: ...xii WatchGuard Firebox System...
Страница 22: ...CHAPTER 1 Internet Protocol Reference 10 WatchGuard Firebox System...
Страница 38: ...CHAPTER 2 MIME Content Types 26 WatchGuard Firebox System...
Страница 92: ...CHAPTER 5 Common Log Messages 80 WatchGuard Firebox System...
Страница 118: ...CHAPTER 8 Firebox Read Only System Area 106 WatchGuard Firebox System...
Страница 164: ...CHAPTER 9 Glossary 152 WatchGuard Firebox System...