CHAPTER 3: Services and Ports
36
WatchGuard Firebox System
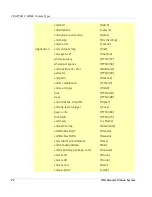
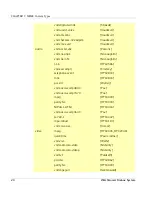
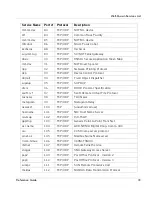
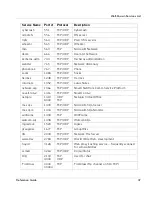
ipx
213
TCP/UDP
IPX
imap3
220
TCP/UDP
Interactive Mail Access Protocol v3
fln-spx
221
TCP/UDP
Berkeley rlogind with SPX auth
rsh-spx
222
TCP/UDP
Berkeley rshd with SPX auth
backweb
371
UDP
BackWeb
ulistserv
372
TCP/UDP
Unix Listserv
netware-ip
396
TCP/UDP
Novell Netware over IP
biff
512
UDP
Used by mail system to notify users
exec
512
TCP
Remote process execution
login
513
TCP/UDP
Login Host Protocol
who
513
UDP
Maintains databases showing who’s who
cmd
514
TCP
Like exec, but automatic
syslog
514
UDP
logging facilities
printer
515
TCP/UDP
Spooler
talk
517
TCP/UDP
Talk protocol
ntalk
518
TCP/UDP
another Talk
utime
519
TCP/UDP
Unixtime
router
520
UDP
RIP local routing process (on site)
timed
525
TCP/UDP
Timeserver
tempo
526
TCP/UDP
Newdate
courier
530
TCP/UDP
Rpc
conference
531
TCP/UDP
Chat
netnews
532
TCP/UDP
Readnews
netwall
533
TCP/UDP
For emergency broadcasts
uucp
540
TCP/UDP
Uucpd
uucp-rlogin
541
TCP/UDP
Uucp-rlogin Stuart Lynne
klogin
543
TCP/UDP
Kerberos (v4/v5)
kshell
544
TCP/UDP
krcmd Kerberos (v4/v5)
dhcpv6-client
546
TCP/UDP
DHCPv6 Client
dhcpv6-server
547
TCP/UDP
DHCPv6 Server
Service Name
Port #
Protocol
Description
Содержание Firebox X1000
Страница 1: ...WatchGuard Firebox System Reference Guide WatchGuard Firebox System...
Страница 12: ...xii WatchGuard Firebox System...
Страница 22: ...CHAPTER 1 Internet Protocol Reference 10 WatchGuard Firebox System...
Страница 38: ...CHAPTER 2 MIME Content Types 26 WatchGuard Firebox System...
Страница 92: ...CHAPTER 5 Common Log Messages 80 WatchGuard Firebox System...
Страница 118: ...CHAPTER 8 Firebox Read Only System Area 106 WatchGuard Firebox System...
Страница 164: ...CHAPTER 9 Glossary 152 WatchGuard Firebox System...