Configuring Access Security
Access Security Configurations
User Guide
705
Protocol V1
Select
Enable
to enable SSH version 1.
Protocol V2
Select
Enable
to enable SSH version 2.
Idle Timeout
Specify the idle timeout time. The system will automatically release the
connection when the time is up.
Maximum
Connections
Specify the maximum number of the connections to the SSH server. New
connection will not be established when the number of the connections reaches
the maximum number you set.
Port
Specify the port using for SSH.
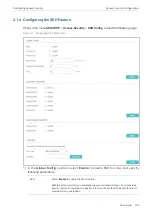
2) In the
Encryption Algorithm
section, enable the encryption algorithm you want the
switch to support and click
Apply
.
3) In
Data Integrity Algorithm
section, enable the integrity algorithm you want the switch
to support and click
Apply
.
4) In
Import Key File
section, select key type from the drop-down list and click
Browse
to
download the desired key file.
Key Type
Select the key type. The algorithm of the corresponding type is used for both key
generation and authentication.
Key File
Select the desired public key to download to the switch. The key length of the
downloaded file ranges of 512 to 3072 bits.
Note:
It will take a long time to download the key file. Please wait without any operation.
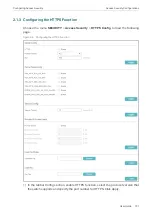
2.1.5 Configuring the Telnet Function
Choose the menu
SECURITY
>
Access Security
>
Telnet Config
to load the following
page.
Figure 2-8
Configuring the Telnet Function
Enable Telnet and click
Apply
.
Telnet
Select
Enable
to make the Telnet function effective. Telnet function is based on the
Telnet protocol subjected to TCP/IP protocol. It allows users to log on to the switch
remotely.
Port
Specify the port using for Telnet.
Содержание JetStream T2600G-28TS
Страница 32: ...Part 1 Accessing the Switch CHAPTERS 1 Overview 2 Web Interface Access 3 Command Line Interface Access ...
Страница 136: ...Part 4 Configuring LAG CHAPTERS 1 LAG 2 LAG Configuration 3 Configuration Examples 4 Appendix Default Parameters ...
Страница 154: ...Part 5 Configuring DDM Only for Certain Devices CHAPTERS 1 Overview 2 DDM Configuration 3 Appendix Default Parameters ...
Страница 264: ...Configuring VLAN VPN Configuration Examples User Guide 235 Figure 4 2 Create VLAN 100 ...
Страница 265: ...User Guide 236 Configuring VLAN VPN Configuration Examples Figure 4 3 Create VLAN 200 ...
Страница 268: ...Configuring VLAN VPN Configuration Examples User Guide 239 Figure 4 7 Creating VLAN 100 ...
Страница 275: ...User Guide 246 Configuring VLAN VPN Configuration Examples Figure 4 11 Create VLAN 100 ...
Страница 276: ...Configuring VLAN VPN Configuration Examples User Guide 247 Figure 4 12 Create VLAN 200 ...
Страница 277: ...User Guide 248 Configuring VLAN VPN Configuration Examples Figure 4 13 Create VLAN 1050 ...
Страница 280: ...Configuring VLAN VPN Configuration Examples User Guide 251 Figure 4 18 Creating VLAN 100 ...
Страница 285: ...Part 11 Configuring GVRP CHAPTERS 1 Overview 2 GVRP Configuration 3 Configuration Example 4 Appendix Default Parameters ...
Страница 512: ...Part 16 Configuring L2PT CHAPTERS 1 Overview 2 L2PT Configuration 3 Configuration Example 4 Appendix Default Parameters ...
Страница 633: ...Part 21 Configuring ARP CHAPTERS 1 Overview 2 ARP Configurations 3 Appendix Default Parameters ...
Страница 718: ...Configuring QoS Configuration Examples User Guide 689 Extended Power Via MDI Yes Inventory Management Yes ...
Страница 748: ...Part 24 Configuring AAA CHAPTERS 1 Overview 2 AAA Configuration 3 Configuration Examples 4 Appendix Default Parameters ...
Страница 801: ...Part 26 Configuring Port Security CHAPTERS 1 Overview 2 Port Security Configuration 3 Appendix Default Parameters ...
Страница 859: ...User Guide 830 Configuring ACL Configuration Example for ACL Figure 3 18 Configuring Rule 3 ...
Страница 874: ...Configuring ACL User Guide 845 ...
Страница 962: ...Part 31 Configuring DoS Defend CHAPTERS 1 Overview 2 DoS Defend Configuration 3 Appendix Default Parameters ...
Страница 969: ...Part 32 Monitoring the System CHAPTERS 1 Overview 2 Monitoring the CPU 3 Monitoring the Memory ...
Страница 974: ...Monitoring the System Monitoring the Memory User Guide 945 Unit Current Memory Utilization 1 74 ...
Страница 975: ...Part 33 Monitoring Traffic CHAPTERS 1 Traffic Monitor 2 Appendix Default Parameters ...
Страница 982: ...Part 34 Mirroring Traffic CHAPTERS 1 Mirroring 2 Configuration Examples 3 Appendix Default Parameters ...
Страница 1043: ...Part 37 Configuring DLDP CHAPTERS 1 Overview 2 DLDP Configuration 3 Appendix Default Parameters ...
Страница 1111: ...User Guide 1082 Appendix Default Parameters Parameter Default Setting Interval 1800 seconds Owner monitor Status Disabled ...
Страница 1112: ...Part 39 Diagnosing the Device Network CHAPTERS 1 Diagnosing the Device 2 Diagnosing the Network 3 Appendix Default Parameters ...