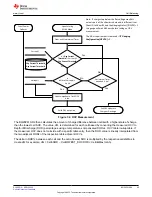
9.4 Authentication
The authentication should be implemented using the following steps:
1. MAC command 0x0000: Command = 0x0000, write the 20 bytes to 0x40, then write the clen at
0x60.
The response will be available as a MAC response, so 0x3E/0x3F will be 0x0000, 0x40 will have the SHA1
result, and 0x60/0x61 will have the checksum and length.
2. Generate 160-bit message M using a random number generator that meets approved random number
generators described in FIPS PUB 140–2.
3. Generate SHA-1 input block B1 of 512 bytes (total input = 128-bit authentication key KD + 160-bit message
M + 1 + 159 0s + 100100000).
4. Generate SHA-1 hash HMAC1 using B1.
5. Generate SHA-1 input block B2 of 512 bytes (total input = 128-bit authentication key KD + 160-bit hash
HMAC1 + 1 + 159 0s + 100100000).
6. Generate SHA-1 hash HMAC2 using B2.
7. With no active
MACData()
data waiting, write 160-bit message M to
MACData()
in the format
0xAABBCCDDEEFFGGHHIIJJKKLLMMNNOOPPQQRRSSTT, where AA is LSB.
8. Wait 250 ms, then read
MACData()
for HMAC3.
9. Compare host HMAC2 with device HMAC3, and if it matches, both host and device have the same key KD
and the device is authenticated.
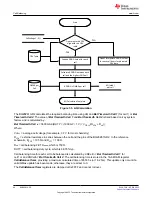
9.5 Security Modes
Changing the security keys requires using the change MAC command; the code to unseal the device can be
sent to 0x3E, 0x3F. The order of the data is in Little Endian. To change the keys, the write operations must be
sent through
MACSubcmd()
0x3E, 0x3F with the
SecurityKey()
followed by the key information. Each parameter
entry must be sent in Little Endian. The 0x3E write block should end after the "0xCD". The checksum and length
are a second command starting at 0x60.
Example:
Changing the Unseal key to 0x0123, 0x4567 and the Full Access key to 0x89AB, 0xCDEF:
Write block: command = 0x3E, block = 0x35 + 0x00 + 0x23 + 0x01 + 0x67 + 0x45 + 0xAB + 0x89 + 0xEF +
0xCD + 1 byte for ch 1 byte for data length. Note: The checksum and length are a second command
starting at 0x60.
Starting address 0x3E, data block (hex) is [35 00 23 01 67 45 ab 89 EF CD], then starting address 0x60, data
block (hex) is [0A 0C] (checksum followed by length) Checksum = 0x0A = ~(0x35 + 0x00 + 0x23 + 0x01 + 0x67
+ 0x45 + 0xAB + 0x89 + 0xEF + 0xCD). The final checksum is the bitwise inversion of the result.
Byte0: Unseal Key LSB
Byte1: Unseal Key MSB
Byte2: Full Access Key LSB
Byte3: Full Access Key MSB
For this activity, the 2nd key must be sent within 4 s of sending the first key; otherwise, the request will not be
accepted.
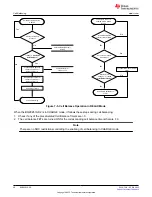
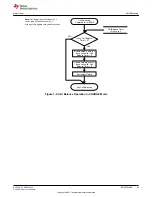
9.5.1 SEALING and UNSEALING Data Flash
The gas gauge has a key access scheme to transition between SEALED, UNSEALED, and FULL ACCESS
modes. Each transition requires that a unique set of two keys be sent to the gas gauge via the
MACSubcmd()
command. The keys must be sent consecutively, with no other data being written to the
MACSubcmd()
register.
The
Seal Device
command instructs the device to limit access to the registers, functions, and data flash space,
and sets the
[SEC1][SEC0]
flags. In SEALED mode, standard register information is accessible. Extended MAC
Commands functions and data flash are not accessible. Once in SEALED mode, the part can never permanently
return to UNSEALED or FULL ACCESS modes.
OperationStatus()
register, shows the
status of the device using
[SEC1][SEC0]
bits.
Device Security
54
BQ28Z610-R2
Copyright © 2022 Texas Instruments Incorporated
Содержание BQ28Z610-R2
Страница 1: ...BQ28Z610 R2 Technical Reference Manual Literature Number SLUUCO0 APRIL 2022 ...
Страница 2: ......