Ruckus Wireless ZoneDirector User Guide | Introducing ZoneDirector
6
FIGURE 1-4
4
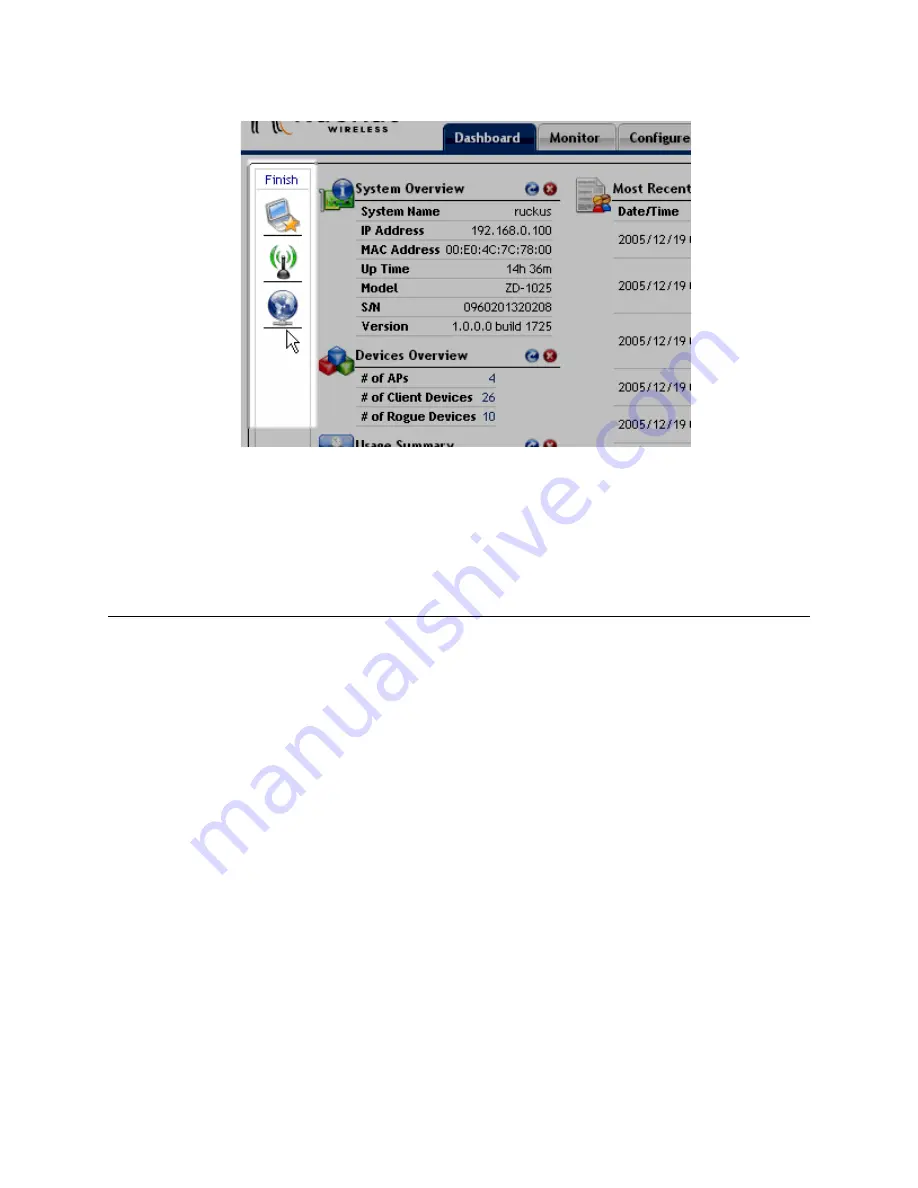
Click
Finish
in the Widgets pane to close it.
Removing a Widget
To remove an indicator widget, click the red x icon for any of the indicator widgets pres-
ently open on the Dashboard.
About Ruckus WLAN Security
After your initial setup, your Ruckus wireless network connects all authorized users by
default to your internal WLAN. This WPA-based WLAN is configured to provide secure cover-
age for all authorized users. (A companion “guest” WLAN provides clear-text but controlled
access for guest users.) But Ruckus offers other security options that can be applied to the
internal WLAN through ZoneDirector. These options range from a less-secure WEP key-based
configuration, through the default WPA passphrase-based configuration to a higher-security,
certificate-based 802.1x EAP configuration. Your choice mostly depends on what kinds of cli-
ent authentication your users' client devices support.
For example, some of your WLAN users may be limited to a WEP-based security system by
their client devices (computer or wireless network adapter). With WebUI, you do have
options: You can regress the existing internal configuration from WPA to the less-secure WEP,
or add a custom WLAN with WEP options for those users who require WEP, while retaining
the original, more secure internal WPA configuration for the rest of your users. Or, you can
replace the default WPA setup with a secure authentication/encryption methodology, 802.1x
EAP.
One drawback to 802.1x is the more labor-intensive setup, requiring (among other tasks) the
transfer of root certificate copies to your users, who must then import the certificates into
their client devices. This will prove disruptive if you have a large user audience already
using your network.

























